Is it best practice to revoke server permissions to the server "public" role on SQL Server instances?
2
votes
2
answers
2470
views
We have evaluated the Microsoft "best practice" policies (located at 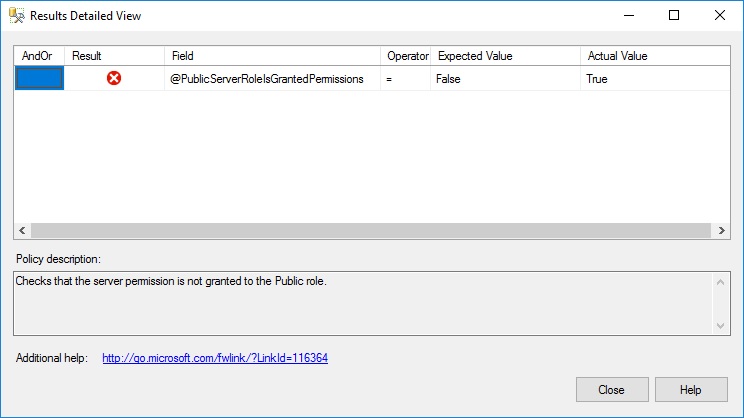 This provides a link to a Microsoft page which states the following as being best practice:
> Do not grant server permissions to the server public role.
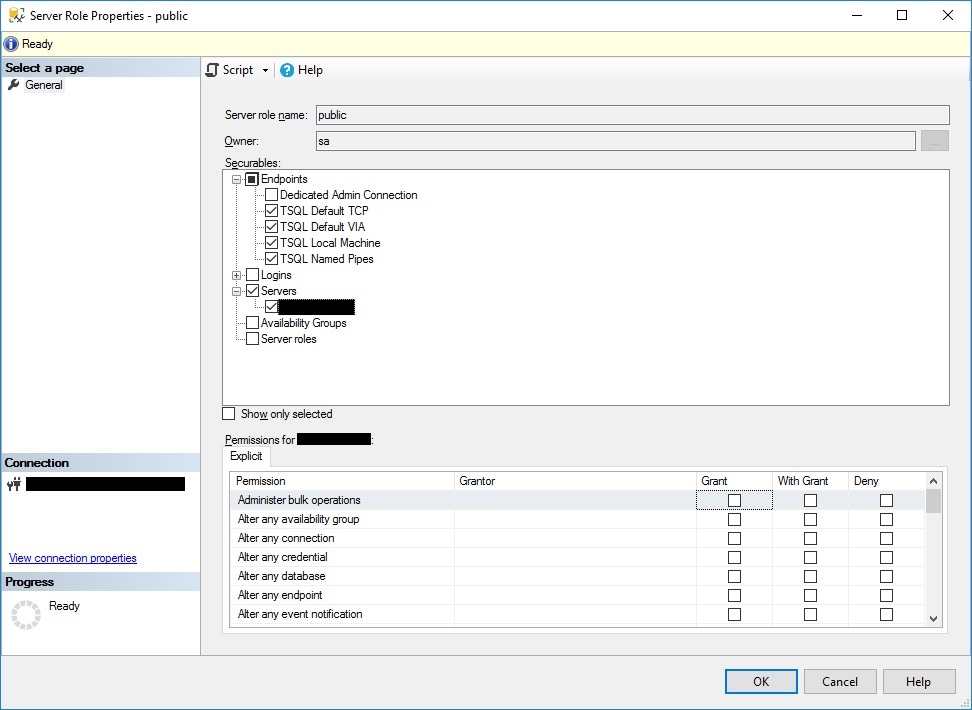
On reviewing the security, we can see that the public role has server permissions to view any database by default. We have run the following and re-evaluated the policy, but the issue is still flagged up.
REVOKE VIEW ANY DATABASE TO [public] AS [sa];
The only other permissions attributed to this server role are endpoint permissions to be able to connect via TCP/VIA/Named Pipes/Local Machine. If we remove these, surely the role will be superfluous.
This provides a link to a Microsoft page which states the following as being best practice:
> Do not grant server permissions to the server public role.
On reviewing the security, we can see that the public role has server permissions to view any database by default. We have run the following and re-evaluated the policy, but the issue is still flagged up.
REVOKE VIEW ANY DATABASE TO [public] AS [sa];
The only other permissions attributed to this server role are endpoint permissions to be able to connect via TCP/VIA/Named Pipes/Local Machine. If we remove these, surely the role will be superfluous.
 **QUESTIONS**
- Should we be concerned about this? Is this something we really should look to address?
- What else do we need to do to properly resolve this issue?
- Are there any implications for doing this or not doing this?
**QUESTIONS**
- Should we be concerned about this? Is this something we really should look to address?
- What else do we need to do to properly resolve this issue?
- Are there any implications for doing this or not doing this?
C:\Program Files (x86)\Microsoft SQL Server\number\Tools\Policies\DatabaseEngine\1033) on each of our SQL Server instances (example here ). The following issue has been flagged up to us:
 This provides a link to a Microsoft page which states the following as being best practice:
> Do not grant server permissions to the server public role.
On reviewing the security, we can see that the public role has server permissions to view any database by default. We have run the following and re-evaluated the policy, but the issue is still flagged up.
REVOKE VIEW ANY DATABASE TO [public] AS [sa];
The only other permissions attributed to this server role are endpoint permissions to be able to connect via TCP/VIA/Named Pipes/Local Machine. If we remove these, surely the role will be superfluous.
This provides a link to a Microsoft page which states the following as being best practice:
> Do not grant server permissions to the server public role.
On reviewing the security, we can see that the public role has server permissions to view any database by default. We have run the following and re-evaluated the policy, but the issue is still flagged up.
REVOKE VIEW ANY DATABASE TO [public] AS [sa];
The only other permissions attributed to this server role are endpoint permissions to be able to connect via TCP/VIA/Named Pipes/Local Machine. If we remove these, surely the role will be superfluous.
 **QUESTIONS**
- Should we be concerned about this? Is this something we really should look to address?
- What else do we need to do to properly resolve this issue?
- Are there any implications for doing this or not doing this?
**QUESTIONS**
- Should we be concerned about this? Is this something we really should look to address?
- What else do we need to do to properly resolve this issue?
- Are there any implications for doing this or not doing this?
Asked by user3399498
(595 rep)
Oct 16, 2018, 10:43 AM
Last activity: Mar 14, 2019, 04:27 PM
Last activity: Mar 14, 2019, 04:27 PM