What's the most effective way to detect nmap scans?
6
votes
3
answers
15574
views
I am interested in detecting any nmap scans directed on a (my) GNU/Linux host. I would like to use snort in combination with barnyard2 and snorby for this, or if possible to perform a signature-based detection on snort unified2 logs. I noticed a similar packet to the following pops up when performing a nmap -A scan:
[ 0] 00 00 FF FF 00 00 00 00 00 00 00 00 00 00 08 00 ................
[ 16] 45 00 00 A2 5C 63 40 00 78 FF 39 03 B9 1E A6 45 E...\c@.x.9....E
[ 32] 05 27 08 D3 50 72 69 6F 72 69 74 79 20 43 6F 75 .'..Priority Cou
[ 48] 6E 74 3A 20 39 0A 43 6F 6E 6E 65 63 74 69 6F 6E nt: 9.Connection
[ 64] 20 43 6F 75 6E 74 3A 20 38 0A 49 50 20 43 6F 75 Count: 8.IP Cou
[ 80] 6E 74 3A 20 32 0A 53 63 61 6E 6E 65 72 20 49 50 nt: 2.Scanner IP
[ 96] 20 52 61 6E 67 65 3A 20 38 34 2E 32 34 32 2E 37 Range: 84.242.7
[ 112] 36 2E 36 36 3A 31 38 35 2E 33 30 2E 31 36 36 2E 6.66:185.30.166.
[ 128] 36 39 0A 50 6F 72 74 2F 50 72 6F 74 6F 20 43 6F 69.Port/Proto Co
[ 144] 75 6E 74 3A 20 31 30 0A 50 6F 72 74 2F 50 72 6F unt: 10.Port/Pro
[ 160] 74 6F to
What's the packet above? Does it have to do with nmap, solely? (I highly doubt that)
Unfortunately snort configured with sfPortscan isn't as effective and/or accurate as I want it to be (Scans are detected but due to some reason I can't see details about it, such as source/destination ::  ,
, 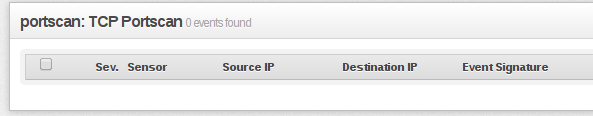 . I have iptables configured with --hitcount and --seconds which makes "stream5: Reset outside window" pop up, thus I can detect a few scans.).
What are my options here?
. I have iptables configured with --hitcount and --seconds which makes "stream5: Reset outside window" pop up, thus I can detect a few scans.).
What are my options here?
 ,
,  . I have iptables configured with --hitcount and --seconds which makes "stream5: Reset outside window" pop up, thus I can detect a few scans.).
What are my options here?
. I have iptables configured with --hitcount and --seconds which makes "stream5: Reset outside window" pop up, thus I can detect a few scans.).
What are my options here?
Asked by niemal010
(95 rep)
Nov 7, 2014, 10:04 PM
Last activity: Dec 20, 2018, 12:13 AM
Last activity: Dec 20, 2018, 12:13 AM