No Traffic via established IKEv2 StrongSWAN Tunnel
1
vote
0
answers
1519
views
I've got a problem I wasn't able to solve in the last days. I've installed StrongSWAN on a Raspberry Pi with Rasbian (Debian GNU/Linux 7.11 (wheezy) / Linux 4.1.19-v7+ armv7l). There is also openVPN running on this Pi. The Subnets are seperated by VLANs (IEEE 802.1q tagged).
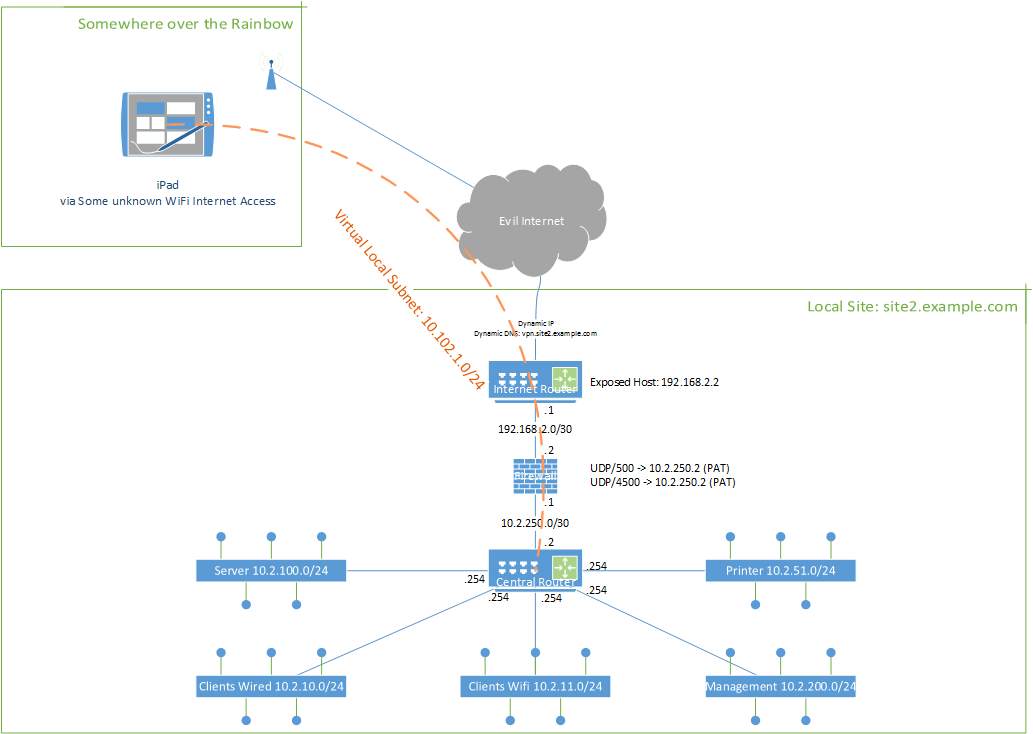 The intention is to connect my IPad from any location to my LAN as I do it already with my Laptop via openVPN. The tunnel is coming up and everything looks good - But the Traffic.
At the moment the Tunnel comes up, I can't access any IP anymore. (At this point I don't want to have Split-Tunneling.) The iPad routing-table looks good
Dest IP/Prefix Gateway IFace
0.0.0.0/0 link#8 ipsec0
0.0.0.0/0 192.168.99.1 (local Gw) en0
10.2.200.254 link#8 ipsec0
The Router itself has no dropping chains in IPTables and no manual rules.
When I ping from the IPad I can't see any traffic from the public source IP on my Firewall. There are only the Keepalives (UDP/500 and UDP/4500). So for me it looks like the iPad isn't sending the payload correct.
200.0.0.1 is the dynamic public IP of the remote client.
**/etc/ipsec.conf**
config setup
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
keyexchange=ikev2
ike=aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes2$
esp=aes128gcm16-ecp256,aes256gcm16-ecp384,aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha$
dpdaction=clear
dpddelay=300s
left=%any
leftsubnet=0.0.0.0/0
leftcert=vpnHostCert.pem
leftid="vpn.site2.example.com"
leftsendcert=always
lefthostaccess=yes
right=%any
rightdns=10.2.200.254
rightid="*@site02.example.com"
rightsourceip=10.102.1.0/24
righthostaccess=yes
conn IPSec-IKEv2
auto=add
**/var/log/syslog**
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] received packet: from 200.0.0.1 to 10.2.250.2 (432 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] looking for an ike config for 10.2.250.2...200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] candidate: %any...%any, prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] found matching ike config: %any...%any with prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] 200.0.0.1 is initiating an IKE_SA
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] IKE_SA (unnamed) state change: CREATED => CONNECTING
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_4096, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_4096, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_4096, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] local host is behind NAT, sending keep alives
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] remote host is behind NAT
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "CN=ca.vpn.site02.example.com, ST=NDS, L=Somewhere, OU=IT, O=Example, C=DE, E=certmaster@example.com"
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (485 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] received packet: from 200.0.0.1 to 10.2.250.2 (1804 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr AUTH CERT CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received end entity cert "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for peer configs matching 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2", match: 20/19/28 (me/other/ike)
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected peer config 'IPSec-IKEv2'
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com" key: 2048 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using trusted ca certificate "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] checking certificate status of "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] ocsp check skipped, no ocsp found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate status is not available
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=Example IPSec CA" key: 4096 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reached self-signed root ca with a path length of 0
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'JohnDoe@site2.example.com' with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_NETMASK attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer supports MOBIKE
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'vpn.site02.example.com' (myself) with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 established between 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 state change: CONNECTING => ESTABLISHED
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] scheduling reauthentication in 9849s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] maximum IKE_SA lifetime 10389s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] sending end entity cert "C=DE, O=Example, CN=vpn.site02.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reassigning offline lease to 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] assigning virtual IP 10.102.1.1 to peer 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any6
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] no virtual IP found for %any6 requested by 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] building INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for a child config for 0.0.0.0/0 ::/0 === 0.0.0.0/0 ::/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2" with prio 10+2
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] found matching child config "IPSec-IKEv2" with prio 12
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] configured proposals: ESP:AES_GCM_16_128/ECP_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_256/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: 0.0.0.0/0 => match: 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: 0.0.0.0/0 => match: 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] CHILD_SA IPSec-IKEv2{2} established with SPIs cfc7c697_i 09e87caf_o and TS 0.0.0.0/0 === 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH CPRP(ADDR DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (1772 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
**iptables-save**
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*nat
:PREROUTING ACCEPT [333:25621]
:INPUT ACCEPT [104:10720]
:OUTPUT ACCEPT [1264:104724]
:POSTROUTING ACCEPT [1493:119625]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*filter
:INPUT ACCEPT [22151:4547969]
:FORWARD ACCEPT [7303:2080414]
:OUTPUT ACCEPT [22707:4537290]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
**iptables**
eth0 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.0.254 Bcast:10.2.0.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507930 errors:0 dropped:0 overruns:0 frame:0
TX packets:510583 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:1000
RX bytes:436916075 (416.6 MiB) TX bytes:448900377 (428.1 MiB)
eth0.10 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.10.254 Bcast:10.2.10.255 Maske:255.255.255.0
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1818 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:497281 (485.6 KiB)
eth0.11 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.11.254 Bcast:10.2.11.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:5857 errors:0 dropped:0 overruns:0 frame:0
TX packets:4833 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:1402095 (1.3 MiB) TX bytes:760454 (742.6 KiB)
eth0.20 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.20.254 Bcast:10.2.20.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1236 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:472837 (461.7 KiB)
eth0.51 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.51.254 Bcast:10.2.51.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:472 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:36720 (35.8 KiB)
eth0.100 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.100.254 Bcast:10.2.100.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:180916 errors:0 dropped:0 overruns:0 frame:0
TX packets:277135 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:52955753 (50.5 MiB) TX bytes:368243511 (351.1 MiB)
eth0.110 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.110.254 Bcast:10.2.110.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507 errors:0 dropped:0 overruns:0 frame:0
TX packets:1713 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:92936 (90.7 KiB) TX bytes:526225 (513.8 KiB)
eth0.150 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.150.254 Bcast:10.2.150.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth0.200 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.200.254 Bcast:10.2.200.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:4945 errors:0 dropped:0 overruns:0 frame:0
TX packets:6059 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:596764 (582.7 KiB) TX bytes:2019159 (1.9 MiB)
eth0.2500 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.250.2 Bcast:10.2.250.3 Maske:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:313144 errors:0 dropped:0 overruns:0 frame:0
TX packets:217317 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:379718967 (362.1 MiB) TX bytes:70217194 (66.9 MiB)
lo Link encap:Lokale Schleife
inet Adresse:127.0.0.1 Maske:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metrik:1
RX packets:27589 errors:0 dropped:0 overruns:0 frame:0
TX packets:27589 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:3368330 (3.2 MiB) TX bytes:3368330 (3.2 MiB)
tun0 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.100.12.2 P-z-P:10.100.12.1 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:19147 errors:0 dropped:0 overruns:0 frame:0
TX packets:19569 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:3915884 (3.7 MiB) TX bytes:2446854 (2.3 MiB)
tun1 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.102.0.1 P-z-P:10.102.0.2 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:11134 errors:0 dropped:0 overruns:0 frame:0
TX packets:11398 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:2738720 (2.6 MiB) TX bytes:7083263 (6.7 MiB)
Any Ideas?
*EDIT 14.10.2016 10:37 CEST:*
**Relevant part of iPMC.mobileconfig**
PayloadDescription
VPN-Setup for site2.example.com_IPSec
PayloadDisplayName
VPN-Config site2.example.com_IPSec
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.config
PayloadType
com.apple.vpn.managed
PayloadUUID
87c9ece2-3e6b-56a4-8bed-2f4cba277d93
PayloadVersion
1
UserDefinedName
site2.example.com_IPSec
VPNType
IKEv2
IKEv2
AuthenticationMethod
Certificate
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
RemoteAddress
vpn.site2.example.com
RemoteIdentifier
vpn.site2.example.com
LocalIdentifier
JohnDoe@site2.example.com
AuthenticationMethod
Certificate
ExtendedAuthEnabled
0
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
OnDemandEnabled
0
IKESecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
ChildSecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
IPv4
OverridePrimary
1
PayloadDisplayName
VPN-CA-Certificate
PayloadDescription
Setup of a VPN-CA-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.cacertificate
PayloadType
com.apple.security.root
PayloadUUID
0b541041-c649-5563-adf9-2d56ed801ad3
PayloadVersion
1
PayloadCertificateFileName
vpn_2_ca.crt
PayloadContent
XX0xXX0XXXxXXxXXXXXXXXXXX0XXXX0xXX0xXx0XXXXXXXXXXXx0
X0X0XXXXX0xXXxxXx0XxXX0XX0X0XXXXXxxxXxxxxxXXXXXXXxXX
XXxXXXXXXXXxX0XxXXXXXxxXX0XXXXxXxxXXXxxXXxXXx0XXx0xx
[... cut away ...]
x0xXXXx0xXXXxXxXxXxXXXxXXxx0xXXxXx0XXxXXXXXxXxxXxXXx
XXXXXXx0X0X0xXx0x0XXXxXXXxX0XXXxXxxxXXxxxXxXXxx0XX0X
XxXxXxxxxX0XXXXXXXXXx0xXXXX0X0XxXxX0Xx0xXX0xXX0XXXXX
XxXXXxxXXXXXXX0xXX0X
PayloadDisplayName
VPN-Client-Certificate
PayloadDescription
Setup of a Client-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.certificate
PayloadType
com.apple.security.pkcs12
PayloadUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
PayloadVersion
1
PayloadCertificateFileName
vpn_2.p12
Password
veryverylongandcomplexpassword;-)
PayloadContent
YYYYyYYYYyYYYYYYYYyYYYy8YYYYYyYYYYYYyyY/YYYYyyYYYyyY
YYyYYYy8YYYYYyYYYyyyyyyyYyYYYYYY8YYYYyYYyyyYYYyYYYyY
YyyYYYy8YYYYYYYyYyYYyyyYYYYYYyYYYyyYyYYYyYYYYy+8yYy8
[... cut away ...]
YYyy8YYyyYyY8yYYYyyyYYy8yyY8YYyYYYyYYYy8YYYYYYYyYyyY
YyYyYY8YYyYyYYYYYyYYYY8YYYYYYYYYyyY8YYyYYyYyYYYYYYY8
YYYyYYYyYYyYYYyYYyYyYYYYYYyyYYy//Yy8yYYY8/8Y8y88yYY/
YYy8y8YyyYY8yYYYYYY=
The intention is to connect my IPad from any location to my LAN as I do it already with my Laptop via openVPN. The tunnel is coming up and everything looks good - But the Traffic.
At the moment the Tunnel comes up, I can't access any IP anymore. (At this point I don't want to have Split-Tunneling.) The iPad routing-table looks good
Dest IP/Prefix Gateway IFace
0.0.0.0/0 link#8 ipsec0
0.0.0.0/0 192.168.99.1 (local Gw) en0
10.2.200.254 link#8 ipsec0
The Router itself has no dropping chains in IPTables and no manual rules.
When I ping from the IPad I can't see any traffic from the public source IP on my Firewall. There are only the Keepalives (UDP/500 and UDP/4500). So for me it looks like the iPad isn't sending the payload correct.
200.0.0.1 is the dynamic public IP of the remote client.
**/etc/ipsec.conf**
config setup
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
keyexchange=ikev2
ike=aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes2$
esp=aes128gcm16-ecp256,aes256gcm16-ecp384,aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha$
dpdaction=clear
dpddelay=300s
left=%any
leftsubnet=0.0.0.0/0
leftcert=vpnHostCert.pem
leftid="vpn.site2.example.com"
leftsendcert=always
lefthostaccess=yes
right=%any
rightdns=10.2.200.254
rightid="*@site02.example.com"
rightsourceip=10.102.1.0/24
righthostaccess=yes
conn IPSec-IKEv2
auto=add
**/var/log/syslog**
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] received packet: from 200.0.0.1 to 10.2.250.2 (432 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] looking for an ike config for 10.2.250.2...200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] candidate: %any...%any, prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] found matching ike config: %any...%any with prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] 200.0.0.1 is initiating an IKE_SA
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] IKE_SA (unnamed) state change: CREATED => CONNECTING
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_4096, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_4096, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_4096, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] local host is behind NAT, sending keep alives
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] remote host is behind NAT
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "CN=ca.vpn.site02.example.com, ST=NDS, L=Somewhere, OU=IT, O=Example, C=DE, E=certmaster@example.com"
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (485 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] received packet: from 200.0.0.1 to 10.2.250.2 (1804 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr AUTH CERT CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received end entity cert "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for peer configs matching 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2", match: 20/19/28 (me/other/ike)
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected peer config 'IPSec-IKEv2'
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com" key: 2048 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using trusted ca certificate "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] checking certificate status of "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] ocsp check skipped, no ocsp found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate status is not available
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=Example IPSec CA" key: 4096 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reached self-signed root ca with a path length of 0
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'JohnDoe@site2.example.com' with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_NETMASK attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer supports MOBIKE
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'vpn.site02.example.com' (myself) with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 established between 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 state change: CONNECTING => ESTABLISHED
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] scheduling reauthentication in 9849s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] maximum IKE_SA lifetime 10389s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] sending end entity cert "C=DE, O=Example, CN=vpn.site02.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reassigning offline lease to 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] assigning virtual IP 10.102.1.1 to peer 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any6
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] no virtual IP found for %any6 requested by 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] building INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for a child config for 0.0.0.0/0 ::/0 === 0.0.0.0/0 ::/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2" with prio 10+2
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] found matching child config "IPSec-IKEv2" with prio 12
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] configured proposals: ESP:AES_GCM_16_128/ECP_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_256/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: 0.0.0.0/0 => match: 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: 0.0.0.0/0 => match: 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] CHILD_SA IPSec-IKEv2{2} established with SPIs cfc7c697_i 09e87caf_o and TS 0.0.0.0/0 === 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH CPRP(ADDR DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (1772 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
**iptables-save**
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*nat
:PREROUTING ACCEPT [333:25621]
:INPUT ACCEPT [104:10720]
:OUTPUT ACCEPT [1264:104724]
:POSTROUTING ACCEPT [1493:119625]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*filter
:INPUT ACCEPT [22151:4547969]
:FORWARD ACCEPT [7303:2080414]
:OUTPUT ACCEPT [22707:4537290]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
**iptables**
eth0 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.0.254 Bcast:10.2.0.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507930 errors:0 dropped:0 overruns:0 frame:0
TX packets:510583 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:1000
RX bytes:436916075 (416.6 MiB) TX bytes:448900377 (428.1 MiB)
eth0.10 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.10.254 Bcast:10.2.10.255 Maske:255.255.255.0
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1818 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:497281 (485.6 KiB)
eth0.11 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.11.254 Bcast:10.2.11.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:5857 errors:0 dropped:0 overruns:0 frame:0
TX packets:4833 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:1402095 (1.3 MiB) TX bytes:760454 (742.6 KiB)
eth0.20 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.20.254 Bcast:10.2.20.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1236 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:472837 (461.7 KiB)
eth0.51 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.51.254 Bcast:10.2.51.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:472 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:36720 (35.8 KiB)
eth0.100 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.100.254 Bcast:10.2.100.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:180916 errors:0 dropped:0 overruns:0 frame:0
TX packets:277135 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:52955753 (50.5 MiB) TX bytes:368243511 (351.1 MiB)
eth0.110 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.110.254 Bcast:10.2.110.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507 errors:0 dropped:0 overruns:0 frame:0
TX packets:1713 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:92936 (90.7 KiB) TX bytes:526225 (513.8 KiB)
eth0.150 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.150.254 Bcast:10.2.150.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth0.200 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.200.254 Bcast:10.2.200.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:4945 errors:0 dropped:0 overruns:0 frame:0
TX packets:6059 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:596764 (582.7 KiB) TX bytes:2019159 (1.9 MiB)
eth0.2500 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.250.2 Bcast:10.2.250.3 Maske:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:313144 errors:0 dropped:0 overruns:0 frame:0
TX packets:217317 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:379718967 (362.1 MiB) TX bytes:70217194 (66.9 MiB)
lo Link encap:Lokale Schleife
inet Adresse:127.0.0.1 Maske:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metrik:1
RX packets:27589 errors:0 dropped:0 overruns:0 frame:0
TX packets:27589 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:3368330 (3.2 MiB) TX bytes:3368330 (3.2 MiB)
tun0 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.100.12.2 P-z-P:10.100.12.1 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:19147 errors:0 dropped:0 overruns:0 frame:0
TX packets:19569 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:3915884 (3.7 MiB) TX bytes:2446854 (2.3 MiB)
tun1 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.102.0.1 P-z-P:10.102.0.2 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:11134 errors:0 dropped:0 overruns:0 frame:0
TX packets:11398 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:2738720 (2.6 MiB) TX bytes:7083263 (6.7 MiB)
Any Ideas?
*EDIT 14.10.2016 10:37 CEST:*
**Relevant part of iPMC.mobileconfig**
PayloadDescription
VPN-Setup for site2.example.com_IPSec
PayloadDisplayName
VPN-Config site2.example.com_IPSec
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.config
PayloadType
com.apple.vpn.managed
PayloadUUID
87c9ece2-3e6b-56a4-8bed-2f4cba277d93
PayloadVersion
1
UserDefinedName
site2.example.com_IPSec
VPNType
IKEv2
IKEv2
AuthenticationMethod
Certificate
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
RemoteAddress
vpn.site2.example.com
RemoteIdentifier
vpn.site2.example.com
LocalIdentifier
JohnDoe@site2.example.com
AuthenticationMethod
Certificate
ExtendedAuthEnabled
0
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
OnDemandEnabled
0
IKESecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
ChildSecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
IPv4
OverridePrimary
1
PayloadDisplayName
VPN-CA-Certificate
PayloadDescription
Setup of a VPN-CA-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.cacertificate
PayloadType
com.apple.security.root
PayloadUUID
0b541041-c649-5563-adf9-2d56ed801ad3
PayloadVersion
1
PayloadCertificateFileName
vpn_2_ca.crt
PayloadContent
XX0xXX0XXXxXXxXXXXXXXXXXX0XXXX0xXX0xXx0XXXXXXXXXXXx0
X0X0XXXXX0xXXxxXx0XxXX0XX0X0XXXXXxxxXxxxxxXXXXXXXxXX
XXxXXXXXXXXxX0XxXXXXXxxXX0XXXXxXxxXXXxxXXxXXx0XXx0xx
[... cut away ...]
x0xXXXx0xXXXxXxXxXxXXXxXXxx0xXXxXx0XXxXXXXXxXxxXxXXx
XXXXXXx0X0X0xXx0x0XXXxXXXxX0XXXxXxxxXXxxxXxXXxx0XX0X
XxXxXxxxxX0XXXXXXXXXx0xXXXX0X0XxXxX0Xx0xXX0xXX0XXXXX
XxXXXxxXXXXXXX0xXX0X
PayloadDisplayName
VPN-Client-Certificate
PayloadDescription
Setup of a Client-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.certificate
PayloadType
com.apple.security.pkcs12
PayloadUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
PayloadVersion
1
PayloadCertificateFileName
vpn_2.p12
Password
veryverylongandcomplexpassword;-)
PayloadContent
YYYYyYYYYyYYYYYYYYyYYYy8YYYYYyYYYYYYyyY/YYYYyyYYYyyY
YYyYYYy8YYYYYyYYYyyyyyyyYyYYYYYY8YYYYyYYyyyYYYyYYYyY
YyyYYYy8YYYYYYYyYyYYyyyYYYYYYyYYYyyYyYYYyYYYYy+8yYy8
[... cut away ...]
YYyy8YYyyYyY8yYYYyyyYYy8yyY8YYyYYYyYYYy8YYYYYYYyYyyY
YyYyYY8YYyYyYYYYYyYYYY8YYYYYYYYYyyY8YYyYYyYyYYYYYYY8
YYYyYYYyYYyYYYyYYyYyYYYYYYyyYYy//Yy8yYYY8/8Y8y88yYY/
YYy8y8YyyYY8yYYYYYY=
 The intention is to connect my IPad from any location to my LAN as I do it already with my Laptop via openVPN. The tunnel is coming up and everything looks good - But the Traffic.
At the moment the Tunnel comes up, I can't access any IP anymore. (At this point I don't want to have Split-Tunneling.) The iPad routing-table looks good
Dest IP/Prefix Gateway IFace
0.0.0.0/0 link#8 ipsec0
0.0.0.0/0 192.168.99.1 (local Gw) en0
10.2.200.254 link#8 ipsec0
The Router itself has no dropping chains in IPTables and no manual rules.
When I ping from the IPad I can't see any traffic from the public source IP on my Firewall. There are only the Keepalives (UDP/500 and UDP/4500). So for me it looks like the iPad isn't sending the payload correct.
200.0.0.1 is the dynamic public IP of the remote client.
**/etc/ipsec.conf**
config setup
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
keyexchange=ikev2
ike=aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes2$
esp=aes128gcm16-ecp256,aes256gcm16-ecp384,aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha$
dpdaction=clear
dpddelay=300s
left=%any
leftsubnet=0.0.0.0/0
leftcert=vpnHostCert.pem
leftid="vpn.site2.example.com"
leftsendcert=always
lefthostaccess=yes
right=%any
rightdns=10.2.200.254
rightid="*@site02.example.com"
rightsourceip=10.102.1.0/24
righthostaccess=yes
conn IPSec-IKEv2
auto=add
**/var/log/syslog**
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] received packet: from 200.0.0.1 to 10.2.250.2 (432 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] looking for an ike config for 10.2.250.2...200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] candidate: %any...%any, prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] found matching ike config: %any...%any with prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] 200.0.0.1 is initiating an IKE_SA
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] IKE_SA (unnamed) state change: CREATED => CONNECTING
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_4096, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_4096, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_4096, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] local host is behind NAT, sending keep alives
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] remote host is behind NAT
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "CN=ca.vpn.site02.example.com, ST=NDS, L=Somewhere, OU=IT, O=Example, C=DE, E=certmaster@example.com"
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (485 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] received packet: from 200.0.0.1 to 10.2.250.2 (1804 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr AUTH CERT CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received end entity cert "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for peer configs matching 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2", match: 20/19/28 (me/other/ike)
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected peer config 'IPSec-IKEv2'
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com" key: 2048 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using trusted ca certificate "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] checking certificate status of "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] ocsp check skipped, no ocsp found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate status is not available
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=Example IPSec CA" key: 4096 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reached self-signed root ca with a path length of 0
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'JohnDoe@site2.example.com' with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_NETMASK attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer supports MOBIKE
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'vpn.site02.example.com' (myself) with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 established between 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 state change: CONNECTING => ESTABLISHED
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] scheduling reauthentication in 9849s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] maximum IKE_SA lifetime 10389s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] sending end entity cert "C=DE, O=Example, CN=vpn.site02.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reassigning offline lease to 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] assigning virtual IP 10.102.1.1 to peer 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any6
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] no virtual IP found for %any6 requested by 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] building INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for a child config for 0.0.0.0/0 ::/0 === 0.0.0.0/0 ::/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2" with prio 10+2
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] found matching child config "IPSec-IKEv2" with prio 12
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] configured proposals: ESP:AES_GCM_16_128/ECP_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_256/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: 0.0.0.0/0 => match: 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: 0.0.0.0/0 => match: 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] CHILD_SA IPSec-IKEv2{2} established with SPIs cfc7c697_i 09e87caf_o and TS 0.0.0.0/0 === 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH CPRP(ADDR DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (1772 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
**iptables-save**
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*nat
:PREROUTING ACCEPT [333:25621]
:INPUT ACCEPT [104:10720]
:OUTPUT ACCEPT [1264:104724]
:POSTROUTING ACCEPT [1493:119625]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*filter
:INPUT ACCEPT [22151:4547969]
:FORWARD ACCEPT [7303:2080414]
:OUTPUT ACCEPT [22707:4537290]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
**iptables**
eth0 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.0.254 Bcast:10.2.0.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507930 errors:0 dropped:0 overruns:0 frame:0
TX packets:510583 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:1000
RX bytes:436916075 (416.6 MiB) TX bytes:448900377 (428.1 MiB)
eth0.10 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.10.254 Bcast:10.2.10.255 Maske:255.255.255.0
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1818 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:497281 (485.6 KiB)
eth0.11 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.11.254 Bcast:10.2.11.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:5857 errors:0 dropped:0 overruns:0 frame:0
TX packets:4833 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:1402095 (1.3 MiB) TX bytes:760454 (742.6 KiB)
eth0.20 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.20.254 Bcast:10.2.20.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1236 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:472837 (461.7 KiB)
eth0.51 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.51.254 Bcast:10.2.51.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:472 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:36720 (35.8 KiB)
eth0.100 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.100.254 Bcast:10.2.100.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:180916 errors:0 dropped:0 overruns:0 frame:0
TX packets:277135 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:52955753 (50.5 MiB) TX bytes:368243511 (351.1 MiB)
eth0.110 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.110.254 Bcast:10.2.110.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507 errors:0 dropped:0 overruns:0 frame:0
TX packets:1713 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:92936 (90.7 KiB) TX bytes:526225 (513.8 KiB)
eth0.150 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.150.254 Bcast:10.2.150.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth0.200 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.200.254 Bcast:10.2.200.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:4945 errors:0 dropped:0 overruns:0 frame:0
TX packets:6059 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:596764 (582.7 KiB) TX bytes:2019159 (1.9 MiB)
eth0.2500 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.250.2 Bcast:10.2.250.3 Maske:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:313144 errors:0 dropped:0 overruns:0 frame:0
TX packets:217317 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:379718967 (362.1 MiB) TX bytes:70217194 (66.9 MiB)
lo Link encap:Lokale Schleife
inet Adresse:127.0.0.1 Maske:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metrik:1
RX packets:27589 errors:0 dropped:0 overruns:0 frame:0
TX packets:27589 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:3368330 (3.2 MiB) TX bytes:3368330 (3.2 MiB)
tun0 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.100.12.2 P-z-P:10.100.12.1 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:19147 errors:0 dropped:0 overruns:0 frame:0
TX packets:19569 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:3915884 (3.7 MiB) TX bytes:2446854 (2.3 MiB)
tun1 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.102.0.1 P-z-P:10.102.0.2 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:11134 errors:0 dropped:0 overruns:0 frame:0
TX packets:11398 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:2738720 (2.6 MiB) TX bytes:7083263 (6.7 MiB)
Any Ideas?
*EDIT 14.10.2016 10:37 CEST:*
**Relevant part of iPMC.mobileconfig**
PayloadDescription
VPN-Setup for site2.example.com_IPSec
PayloadDisplayName
VPN-Config site2.example.com_IPSec
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.config
PayloadType
com.apple.vpn.managed
PayloadUUID
87c9ece2-3e6b-56a4-8bed-2f4cba277d93
PayloadVersion
1
UserDefinedName
site2.example.com_IPSec
VPNType
IKEv2
IKEv2
AuthenticationMethod
Certificate
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
RemoteAddress
vpn.site2.example.com
RemoteIdentifier
vpn.site2.example.com
LocalIdentifier
JohnDoe@site2.example.com
AuthenticationMethod
Certificate
ExtendedAuthEnabled
0
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
OnDemandEnabled
0
IKESecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
ChildSecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
IPv4
OverridePrimary
1
PayloadDisplayName
VPN-CA-Certificate
PayloadDescription
Setup of a VPN-CA-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.cacertificate
PayloadType
com.apple.security.root
PayloadUUID
0b541041-c649-5563-adf9-2d56ed801ad3
PayloadVersion
1
PayloadCertificateFileName
vpn_2_ca.crt
PayloadContent
XX0xXX0XXXxXXxXXXXXXXXXXX0XXXX0xXX0xXx0XXXXXXXXXXXx0
X0X0XXXXX0xXXxxXx0XxXX0XX0X0XXXXXxxxXxxxxxXXXXXXXxXX
XXxXXXXXXXXxX0XxXXXXXxxXX0XXXXxXxxXXXxxXXxXXx0XXx0xx
[... cut away ...]
x0xXXXx0xXXXxXxXxXxXXXxXXxx0xXXxXx0XXxXXXXXxXxxXxXXx
XXXXXXx0X0X0xXx0x0XXXxXXXxX0XXXxXxxxXXxxxXxXXxx0XX0X
XxXxXxxxxX0XXXXXXXXXx0xXXXX0X0XxXxX0Xx0xXX0xXX0XXXXX
XxXXXxxXXXXXXX0xXX0X
PayloadDisplayName
VPN-Client-Certificate
PayloadDescription
Setup of a Client-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.certificate
PayloadType
com.apple.security.pkcs12
PayloadUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
PayloadVersion
1
PayloadCertificateFileName
vpn_2.p12
Password
veryverylongandcomplexpassword;-)
PayloadContent
YYYYyYYYYyYYYYYYYYyYYYy8YYYYYyYYYYYYyyY/YYYYyyYYYyyY
YYyYYYy8YYYYYyYYYyyyyyyyYyYYYYYY8YYYYyYYyyyYYYyYYYyY
YyyYYYy8YYYYYYYyYyYYyyyYYYYYYyYYYyyYyYYYyYYYYy+8yYy8
[... cut away ...]
YYyy8YYyyYyY8yYYYyyyYYy8yyY8YYyYYYyYYYy8YYYYYYYyYyyY
YyYyYY8YYyYyYYYYYyYYYY8YYYYYYYYYyyY8YYyYYyYyYYYYYYY8
YYYyYYYyYYyYYYyYYyYyYYYYYYyyYYy//Yy8yYYY8/8Y8y88yYY/
YYy8y8YyyYY8yYYYYYY=
The intention is to connect my IPad from any location to my LAN as I do it already with my Laptop via openVPN. The tunnel is coming up and everything looks good - But the Traffic.
At the moment the Tunnel comes up, I can't access any IP anymore. (At this point I don't want to have Split-Tunneling.) The iPad routing-table looks good
Dest IP/Prefix Gateway IFace
0.0.0.0/0 link#8 ipsec0
0.0.0.0/0 192.168.99.1 (local Gw) en0
10.2.200.254 link#8 ipsec0
The Router itself has no dropping chains in IPTables and no manual rules.
When I ping from the IPad I can't see any traffic from the public source IP on my Firewall. There are only the Keepalives (UDP/500 and UDP/4500). So for me it looks like the iPad isn't sending the payload correct.
200.0.0.1 is the dynamic public IP of the remote client.
**/etc/ipsec.conf**
config setup
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
keyexchange=ikev2
ike=aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha1-modp1536,aes256-sha384-modp2048,aes2$
esp=aes128gcm16-ecp256,aes256gcm16-ecp384,aes128-sha256-ecp256,aes256-sha384-ecp384,aes128-sha256-modp2048,aes128-sha1-modp2048,aes256-sha384-modp4096,aes256-sha256-modp4096,aes256-sha1-modp4096,aes128-sha256-modp1536,aes128-sha$
dpdaction=clear
dpddelay=300s
left=%any
leftsubnet=0.0.0.0/0
leftcert=vpnHostCert.pem
leftid="vpn.site2.example.com"
leftsendcert=always
lefthostaccess=yes
right=%any
rightdns=10.2.200.254
rightid="*@site02.example.com"
rightsourceip=10.102.1.0/24
righthostaccess=yes
conn IPSec-IKEv2
auto=add
**/var/log/syslog**
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] received packet: from 200.0.0.1 to 10.2.250.2 (432 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] looking for an ike config for 10.2.250.2...200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] candidate: %any...%any, prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] found matching ike config: %any...%any with prio 28
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] 200.0.0.1 is initiating an IKE_SA
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] IKE_SA (unnamed) state change: CREATED => CONNECTING
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] no acceptable PSEUDO_RANDOM_FUNCTION found
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_4096, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_4096, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_4096, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/MODP_1024, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Oct 13 13:18:02 RTR-200-254 charon: 06[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] local host is behind NAT, sending keep alives
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] remote host is behind NAT
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 06[IKE] sending cert request for "CN=ca.vpn.site02.example.com, ST=NDS, L=Somewhere, OU=IT, O=Example, C=DE, E=certmaster@example.com"
Oct 13 13:18:02 RTR-200-254 charon: 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
Oct 13 13:18:02 RTR-200-254 charon: 06[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (485 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] received packet: from 200.0.0.1 to 10.2.250.2
Oct 13 13:18:02 RTR-200-254 charon: 02[NET] waiting for data on sockets
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] received packet: from 200.0.0.1 to 10.2.250.2 (1804 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr AUTH CERT CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received end entity cert "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for peer configs matching 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2", match: 20/19/28 (me/other/ike)
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected peer config 'IPSec-IKEv2'
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=JohnDoe@site2.example.com" key: 2048 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] using trusted ca certificate "C=DE, O=Example, CN=Example IPSec CA"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] checking certificate status of "C=DE, O=Example, CN=JohnDoe@site2.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] ocsp check skipped, no ocsp found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate status is not available
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] certificate "C=DE, O=Example, CN=Example IPSec CA" key: 4096 bit RSA
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reached self-signed root ca with a path length of 0
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'JohnDoe@site2.example.com' with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP4_NETMASK attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_ADDRESS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DHCP attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] processing INTERNAL_IP6_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer supports MOBIKE
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] authentication of 'vpn.site02.example.com' (myself) with RSA signature successful
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 established between 10.2.250.2[vpn.site02.example.com]...200.0.0.1[JohnDoe@site2.example.com]
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] IKE_SA IPSec-IKEv2 state change: CONNECTING => ESTABLISHED
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] scheduling reauthentication in 9849s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] maximum IKE_SA lifetime 10389s
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] sending end entity cert "C=DE, O=Example, CN=vpn.site02.example.com"
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] reassigning offline lease to 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] assigning virtual IP 10.102.1.1 to peer 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] peer requested virtual IP %any6
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] no virtual IP found for %any6 requested by 'JohnDoe@site2.example.com'
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] building INTERNAL_IP4_DNS attribute
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] looking for a child config for 0.0.0.0/0 ::/0 === 0.0.0.0/0 ::/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposing traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] candidate "IPSec-IKEv2" with prio 10+2
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] found matching child config "IPSec-IKEv2" with prio 12
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable ENCRYPTION_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] no acceptable INTEGRITY_ALGORITHM found
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting proposal:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] proposal matches
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] received proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] configured proposals: ESP:AES_GCM_16_128/ECP_256/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/ECP_256/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_4096/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_2048/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1536/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_1024/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for us:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: 0.0.0.0/0 => match: 0.0.0.0/0
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 0.0.0.0/0, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] selecting traffic selectors for other:
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: 0.0.0.0/0 => match: 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[CFG] config: 10.102.1.1/32, received: ::/0 => no match
Oct 13 13:18:02 RTR-200-254 charon: 05[IKE] CHILD_SA IPSec-IKEv2{2} established with SPIs cfc7c697_i 09e87caf_o and TS 0.0.0.0/0 === 10.102.1.1/32
Oct 13 13:18:02 RTR-200-254 charon: 05[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH CPRP(ADDR DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Oct 13 13:18:02 RTR-200-254 charon: 05[NET] sending packet: from 10.2.250.2 to 200.0.0.1 (1772 bytes)
Oct 13 13:18:02 RTR-200-254 charon: 03[NET] sending packet: from 10.2.250.2 to 200.0.0.1
**iptables-save**
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*nat
:PREROUTING ACCEPT [333:25621]
:INPUT ACCEPT [104:10720]
:OUTPUT ACCEPT [1264:104724]
:POSTROUTING ACCEPT [1493:119625]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
# Generated by iptables-save v1.4.14 on Thu Oct 13 13:25:44 2016
*filter
:INPUT ACCEPT [22151:4547969]
:FORWARD ACCEPT [7303:2080414]
:OUTPUT ACCEPT [22707:4537290]
COMMIT
# Completed on Thu Oct 13 13:25:44 2016
**iptables**
eth0 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.0.254 Bcast:10.2.0.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507930 errors:0 dropped:0 overruns:0 frame:0
TX packets:510583 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:1000
RX bytes:436916075 (416.6 MiB) TX bytes:448900377 (428.1 MiB)
eth0.10 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.10.254 Bcast:10.2.10.255 Maske:255.255.255.0
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1818 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:497281 (485.6 KiB)
eth0.11 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.11.254 Bcast:10.2.11.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:5857 errors:0 dropped:0 overruns:0 frame:0
TX packets:4833 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:1402095 (1.3 MiB) TX bytes:760454 (742.6 KiB)
eth0.20 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.20.254 Bcast:10.2.20.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:1236 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:472837 (461.7 KiB)
eth0.51 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.51.254 Bcast:10.2.51.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:472 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:36720 (35.8 KiB)
eth0.100 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.100.254 Bcast:10.2.100.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:180916 errors:0 dropped:0 overruns:0 frame:0
TX packets:277135 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:52955753 (50.5 MiB) TX bytes:368243511 (351.1 MiB)
eth0.110 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.110.254 Bcast:10.2.110.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:507 errors:0 dropped:0 overruns:0 frame:0
TX packets:1713 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:92936 (90.7 KiB) TX bytes:526225 (513.8 KiB)
eth0.150 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.150.254 Bcast:10.2.150.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth0.200 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.200.254 Bcast:10.2.200.255 Maske:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:4945 errors:0 dropped:0 overruns:0 frame:0
TX packets:6059 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:596764 (582.7 KiB) TX bytes:2019159 (1.9 MiB)
eth0.2500 Link encap:Ethernet Hardware Adresse 11:22:33:44:55:66
inet Adresse:10.2.250.2 Bcast:10.2.250.3 Maske:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metrik:1
RX packets:313144 errors:0 dropped:0 overruns:0 frame:0
TX packets:217317 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:379718967 (362.1 MiB) TX bytes:70217194 (66.9 MiB)
lo Link encap:Lokale Schleife
inet Adresse:127.0.0.1 Maske:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metrik:1
RX packets:27589 errors:0 dropped:0 overruns:0 frame:0
TX packets:27589 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:0
RX bytes:3368330 (3.2 MiB) TX bytes:3368330 (3.2 MiB)
tun0 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.100.12.2 P-z-P:10.100.12.1 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:19147 errors:0 dropped:0 overruns:0 frame:0
TX packets:19569 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:3915884 (3.7 MiB) TX bytes:2446854 (2.3 MiB)
tun1 Link encap:UNSPEC Hardware Adresse 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet Adresse:10.102.0.1 P-z-P:10.102.0.2 Maske:255.255.255.255
UP PUNKTZUPUNKT RUNNING NOARP MULTICAST MTU:1500 Metrik:1
RX packets:11134 errors:0 dropped:0 overruns:0 frame:0
TX packets:11398 errors:0 dropped:0 overruns:0 carrier:0
Kollisionen:0 Sendewarteschlangenlänge:100
RX bytes:2738720 (2.6 MiB) TX bytes:7083263 (6.7 MiB)
Any Ideas?
*EDIT 14.10.2016 10:37 CEST:*
**Relevant part of iPMC.mobileconfig**
PayloadDescription
VPN-Setup for site2.example.com_IPSec
PayloadDisplayName
VPN-Config site2.example.com_IPSec
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.config
PayloadType
com.apple.vpn.managed
PayloadUUID
87c9ece2-3e6b-56a4-8bed-2f4cba277d93
PayloadVersion
1
UserDefinedName
site2.example.com_IPSec
VPNType
IKEv2
IKEv2
AuthenticationMethod
Certificate
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
RemoteAddress
vpn.site2.example.com
RemoteIdentifier
vpn.site2.example.com
LocalIdentifier
JohnDoe@site2.example.com
AuthenticationMethod
Certificate
ExtendedAuthEnabled
0
PayloadCertificateUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
OnDemandEnabled
0
IKESecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
ChildSecurityAssociationParameters
EncryptionAlgorithm
AES-128
IntegrityAlgorithm
SHA1-96
DiffieHellmanGroup
14
IPv4
OverridePrimary
1
PayloadDisplayName
VPN-CA-Certificate
PayloadDescription
Setup of a VPN-CA-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.cacertificate
PayloadType
com.apple.security.root
PayloadUUID
0b541041-c649-5563-adf9-2d56ed801ad3
PayloadVersion
1
PayloadCertificateFileName
vpn_2_ca.crt
PayloadContent
XX0xXX0XXXxXXxXXXXXXXXXXX0XXXX0xXX0xXx0XXXXXXXXXXXx0
X0X0XXXXX0xXXxxXx0XxXX0XX0X0XXXXXxxxXxxxxxXXXXXXXxXX
XXxXXXXXXXXxX0XxXXXXXxxXX0XXXXxXxxXXXxxXXxXXx0XXx0xx
[... cut away ...]
x0xXXXx0xXXXxXxXxXxXXXxXXxx0xXXxXx0XXxXXXXXxXxxXxXXx
XXXXXXx0X0X0xXx0x0XXXxXXXxX0XXXxXxxxXXxxxXxXXxx0XX0X
XxXxXxxxxX0XXXXXXXXXx0xXXXX0X0XxXxX0Xx0xXX0xXX0XXXXX
XxXXXxxXXXXXXX0xXX0X
PayloadDisplayName
VPN-Client-Certificate
PayloadDescription
Setup of a Client-Certificate
PayloadIdentifier
com.example.admin.JohnDoe.vpn.2.certificate
PayloadType
com.apple.security.pkcs12
PayloadUUID
7d35ed5d-5f97-55c8-b668-254fe57e26d4
PayloadVersion
1
PayloadCertificateFileName
vpn_2.p12
Password
veryverylongandcomplexpassword;-)
PayloadContent
YYYYyYYYYyYYYYYYYYyYYYy8YYYYYyYYYYYYyyY/YYYYyyYYYyyY
YYyYYYy8YYYYYyYYYyyyyyyyYyYYYYYY8YYYYyYYyyyYYYyYYYyY
YyyYYYy8YYYYYYYyYyYYyyyYYYYYYyYYYyyYyYYYyYYYYy+8yYy8
[... cut away ...]
YYyy8YYyyYyY8yYYYyyyYYy8yyY8YYyYYYyYYYy8YYYYYYYyYyyY
YyYyYY8YYyYyYYYYYyYYYY8YYYYYYYYYyyY8YYyYYyYyYYYYYYY8
YYYyYYYyYYyYYYyYYyYyYYYYYYyyYYy//Yy8yYYY8/8Y8y88yYY/
YYy8y8YyyYY8yYYYYYY=
Asked by Skjall
(11 rep)
Oct 13, 2016, 01:44 PM
Last activity: Oct 17, 2016, 08:27 AM
Last activity: Oct 17, 2016, 08:27 AM