Extracting a CA Certificate from an Enterprise WiFi (EAP) Network
2
votes
1
answer
3485
views
I have a work network which is an EAP enterprise WiFi network using 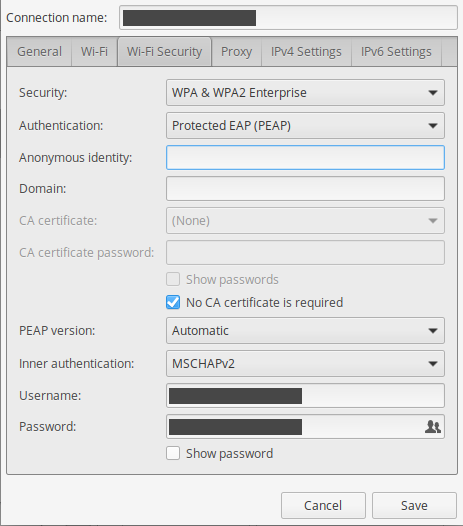
PEAP and MSCHAPv2. I unfortunately don't have the CA certificate for the network, which presumably makes it trivial to harvest my credentials by spoofing the network.
Is there a way for me to fetch the CA presented by the WiFi network so I can set it as the CA certificate to prevent spoofing?
---
**EDIT**: According to [Wikipedia on PEAP](https://en.wikipedia.org/wiki/Protected_Extensible_Authentication_Protocol) , the WiFi server uses a CA for signing its server-side certificate for trust:
> A CA certificate must be used at each client to authenticate the server to each client before the client submits authentication credentials. If the CA certificate is not validated, in general it is trivial to introduce a fake Wireless Access Point which then allows gathering of MS-CHAPv2 handshakes.
I need to get this CA certificate somehow from the server, as I'm sure it issues a certificate chain with the server public key certificate and the CA public key certificate. Presently it is configured without a CA certificate, allowing arbitrary spoofing:

Asked by Naftuli Kay
(41346 rep)
Feb 8, 2019, 06:44 PM
Last activity: Oct 12, 2022, 06:59 PM
Last activity: Oct 12, 2022, 06:59 PM