I'm working on trying to set up a roadwarrior client scenarion VPN with Stringswan on a raspberry pi.
The server config looks like this:
pi@raspberrypi:~ $ sudo cat /etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
config setup
uniqueids=never
charondebug="cfg 2, dmn 2, ike 2, net 2"
conn %default
auto=add
keyexchange=ikev2
ike=aes128-sha256-ecp256
esp=aes128-sha256-ecp256
dpdaction=clear
dpddelay=300s
dpdtimeout = 5s
forceencaps=yes
fragmentation=yes
keyingtries=5
rekey=yes
left=%any
leftfirewall=yes
leftid=MYDNSNAME
leftsubnet=0.0.0.0/0
leftcert=vpnGatewayCert.pem
leftsendcert=always
mobike=yes
right=%any
rightdns=1.1.1.1,1.0.0.1
rightsourceip=192.168.122.101/24 ## LOCAL IP RANGE FOR VPN CONNECTED DEVICES
type=tunnel
conn IKEv2
rightauth=pubkey
include /var/lib/strongswan/ipsec.conf.inc
I also modified the secrets like this:
nano /etc/ipsec.secrets
# This file holds shared secrets or RSA private keys for authentication.
# RSA private key for this host, authenticating it to any other host
# which knows the public part.
# this file is managed with debconf and will contain the automatically created $
include /var/lib/strongswan/ipsec.secrets.inc
: ECDSA vpnGatewayKey.pem
I also created a CA on the raspberry pi, created the strongswan certificates and created a client certificate bundle .p12 file with the following commands:
cd /etc/ipsec.d/
#creating CA Key
ipsec pki --gen --type ecdsa --size 521 --outform pem > private/CA_strongswanKey.pem
chmod 600 private/CA_strongswanKey.pem
#creating CA certificate
ipsec pki --self --ca --lifetime 3650 --in private/CA_strongswanKey.pem --type ecdsa --dn "C=CH, O=strongSwan, CN=strongSwan Root CA" --outform pem > cacerts/CA_strongswanCert.pem
#creating server key
ipsec pki --gen --type ecdsa --size 521 --outform pem > private/vpnGatewayKey.pem
chmod 600 private/vpnGatewayKey.pem
#creating serverCert
ipsec pki --pub --in private/vpnGatewayKey.pem --type ecdsa | \
ipsec pki --issue --lifetime 730 \
--cacert cacerts/CA_strongswanCert.pem \
--cakey private/CA_strongswanKey.pem \
--dn "C=CH, O=strongSwan, CN=MYDNSNAME" \
--san MYDNSNAME \
--flag serverAuth --flag ikeIntermediate \
--outform pem > certs/vpnGatewayCert.pem
#Client Key
ipsec pki --gen --type ecdsa --size 521 --outform pem > private/ClientKey.pem
chmod 600 private/ClientKey.pem
#Client cert
ipsec pki --pub --in private/ClientKey.pem --type ecdsa | \
ipsec pki --issue --lifetime 730 \
--cacert cacerts/CA_strongswanCert.pem \
--cakey private/CA_strongswanKey.pem \
--dn "C=CH, O=strongSwan, CN=Client Key" \
--san Client_Key \
--outform pem > certs/ClientCert.pem
#Exporting client bundle
openssl pkcs12 -export -inkey private/ClientKey.pem \
-in certs/ClientCert.pem -name "Client's VPN Certificate" \
-certfile cacerts/CA_strongswanCert.pem \
-caname "strongSwan Root CA" \
-out Client.p12
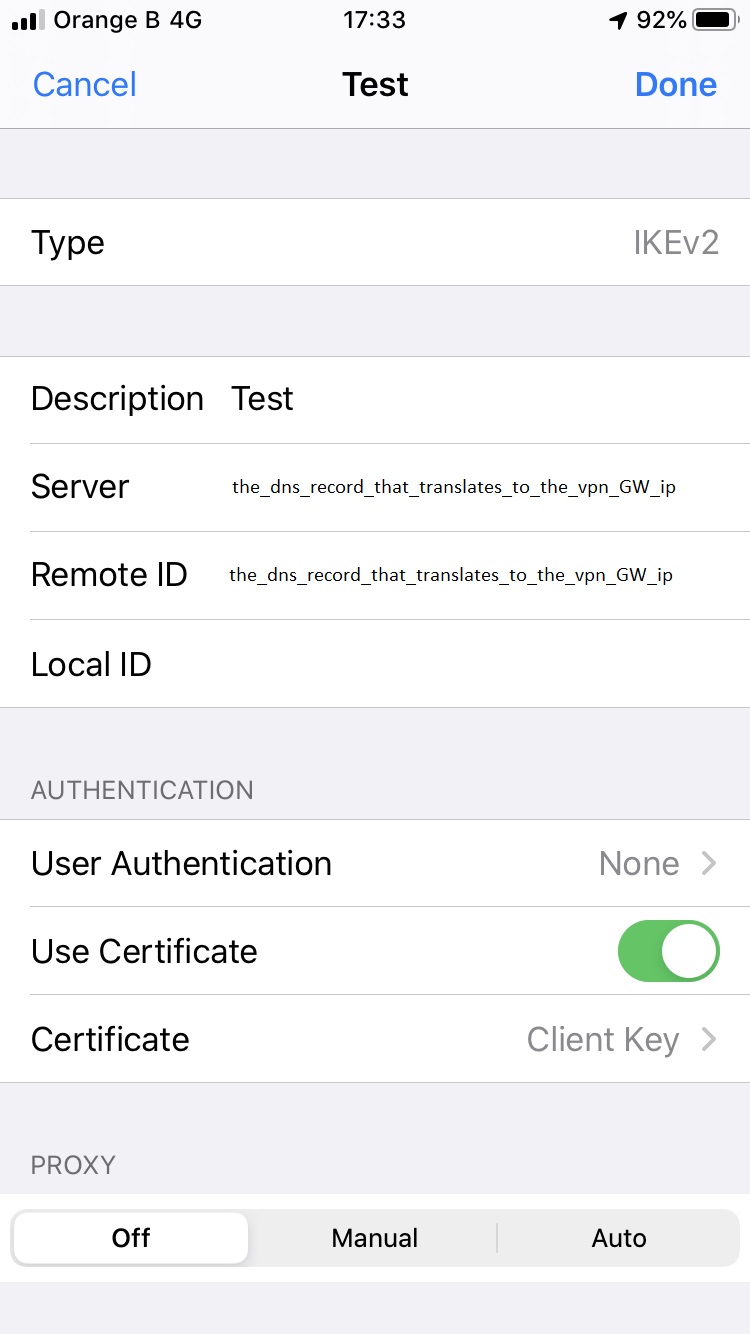
Now I checked and made sure port 500 and 4500 are properly forwarded to the raspberry pi. I downloaded over the .p12 file made in the previous step to my iphone and imported it as a profile. I also imported the vpnGatewayCert.pem and the CA_strongswanCert.pem into my iPhone so it would trust the ipsec gateway server!
When I try to connect the IPhone to the vpn I get an error on the iphone. In the logs of strongswan I see this:
Sep 29 16:18:45 raspberrypi charon: 13[IKE] received end entity cert "C=CH, O=strongSwan, CN=Client Key"
Sep 29 16:18:45 raspberrypi charon: 13[CFG] looking for peer configs matching 192.168.123.101[myDNSNAME]...94.109.49.167[10.218.49.167]
Sep 29 16:18:45 raspberrypi charon: 13[CFG] candidate "IKEv2", match: 20/1/28 (me/other/ike)
Sep 29 16:18:45 raspberrypi charon: 13[CFG] selected peer config 'IKEv2'
Sep 29 16:18:45 raspberrypi charon: 13[IKE] no trusted RSA public key found for '10.218.49.167'
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP4_ADDRESS attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP4_NETMASK attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP4_DHCP attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP4_DNS attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP6_ADDRESS attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP6_DHCP attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing INTERNAL_IP6_DNS attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] processing (25) attribute
Sep 29 16:18:45 raspberrypi charon: 13[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Sep 29 16:18:45 raspberrypi charon: 13[IKE] peer supports MOBIKE
Sep 29 16:18:45 raspberrypi charon: 13[ENC] generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Sep 29 16:18:45 raspberrypi charon: 13[NET] sending packet: from 192.168.123.101 to 94.109.49.167 (80 bytes)
Sep 29 16:18:45 raspberrypi charon: 04[NET] sending packet: from 192.168.123.101 to 94.109.49.167
Sep 29 16:18:45 raspberrypi charon: 13[IKE] IKE_SA IKEv2 state change: CONNECTING => DESTROYING

Asked by user374135
(1 rep)
Sep 29, 2019, 12:37 PM
Last activity: Sep 30, 2019, 08:03 AM
Last activity: Sep 30, 2019, 08:03 AM