Port forwarding with iptables and firejail sandbox
3
votes
1
answer
744
views
I try to run a HTTP server on port 8000 in a firejail sandbox, and make it accessible on all interfaces of the host on port 8888.
The whole system can be represented as below:
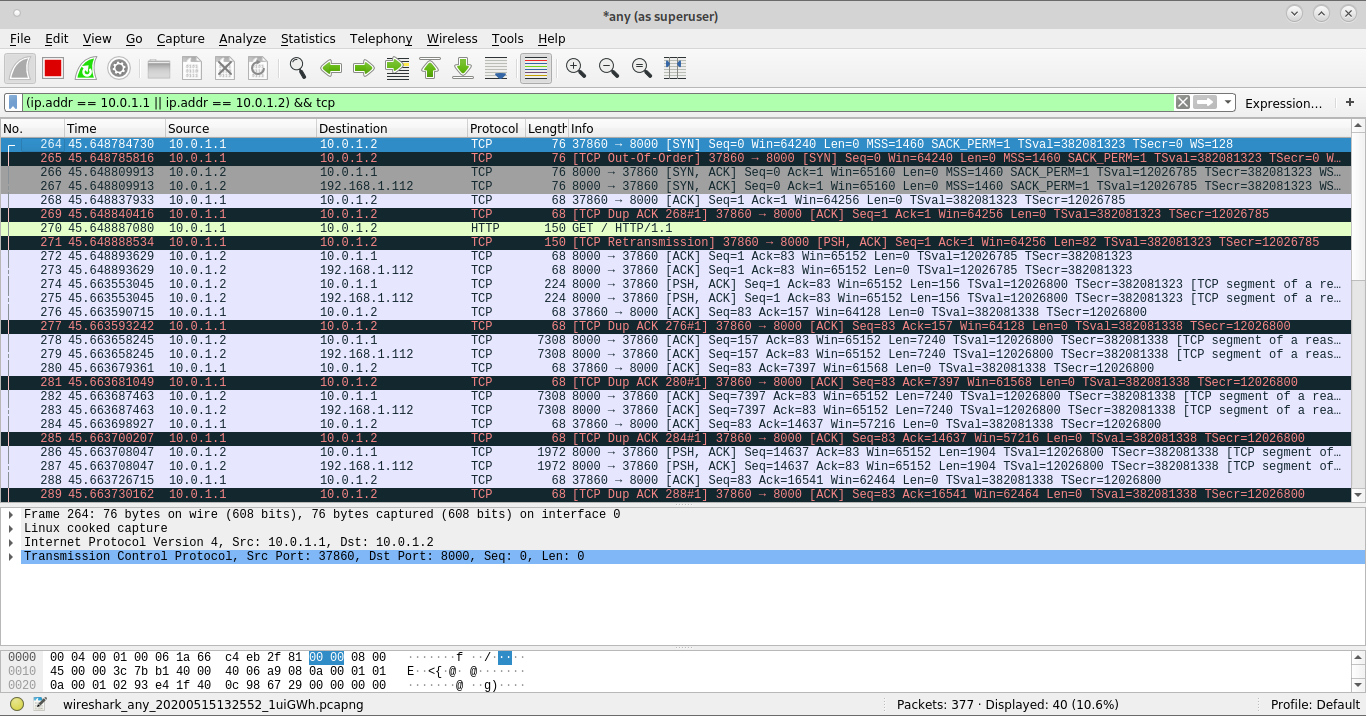 But it doesn't work with a remote host on the same network:
But it doesn't work with a remote host on the same network:
 It seems like the request is not well forwarded to the bridge interface.
Below is the complete list of iptables rules on host-112:
It seems like the request is not well forwarded to the bridge interface.
Below is the complete list of iptables rules on host-112:
+----------------------------------------------------+ +-------------+
| host-112 | | host-238 |
| | +-------+ | |
| +--------------------------+ +-----+ | 192.168.1.112 | | 192.168.1.238 | +----+ |
| | firejail | |wlan0+------------------+ NAT +-------------------+eth0| |
| | | +-----+ | | | | +----+ |
| | | | +-------+ | |
| | +----+ 10.0.1.2 | 10.0.1.1 +------+ | | |
| | |eth0+--------------------------+my_br0| | | |
| | +----+ | +------+ | | |
| | | | | |
| | | | | |
| | HTTP server
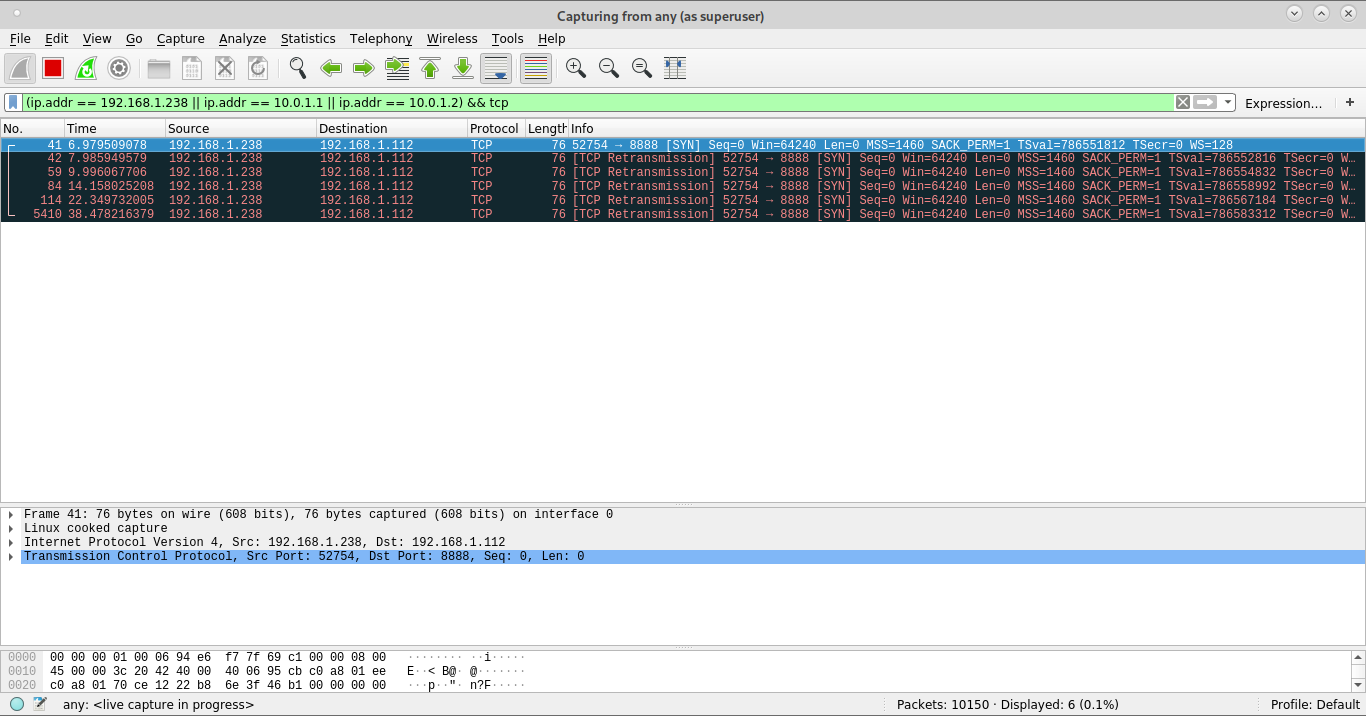
... But it doesn't work with a remote host on the same network:
But it doesn't work with a remote host on the same network:
lang-bash
myself@host-238 $ curl 192.168.1.112:8888
curl: (7) Failed to connect to 192.168.1.112 port 8888: Connection timed out It seems like the request is not well forwarded to the bridge interface.
Below is the complete list of iptables rules on host-112:
It seems like the request is not well forwarded to the bridge interface.
Below is the complete list of iptables rules on host-112:
lang-bash
# iptables -S
-P INPUT ACCEPT
-P FORWARD DROP
-P OUTPUT ACCEPT
-N DOCKER
-N DOCKER-ISOLATION-STAGE-1
-N DOCKER-ISOLATION-STAGE-2
-N DOCKER-USER
-A INPUT -i my_br0 -p tcp -m tcp --sport 8000 -j ACCEPT
-A FORWARD -j DOCKER-USER
-A FORWARD -j DOCKER-ISOLATION-STAGE-1
-A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -o docker0 -j DOCKER
-A FORWARD -i docker0 ! -o docker0 -j ACCEPT
-A FORWARD -i docker0 -o docker0 -j ACCEPT
-A FORWARD -i my_br0 -p tcp -m tcp --dport 8000 -j ACCEPT
-A DOCKER-ISOLATION-STAGE-1 -i docker0 ! -o docker0 -j DOCKER-ISOLATION-STAGE-2
-A DOCKER-ISOLATION-STAGE-1 -j RETURN
-A DOCKER-ISOLATION-STAGE-2 -o docker0 -j DROP
-A DOCKER-ISOLATION-STAGE-2 -j RETURN
-A DOCKER-USER -j RETURN
# iptables -S -t nat
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P POSTROUTING ACCEPT
-P OUTPUT ACCEPT
-N DOCKER
-A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
-A PREROUTING -p tcp -m tcp --dport 8888 -j DNAT --to-destination 10.0.1.2:8000
-A POSTROUTING -s 172.19.0.0/16 ! -o docker0 -j MASQUERADE
-A POSTROUTING -o my_br0 -p tcp -j MASQUERADE
-A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER
-A OUTPUT -p tcp -m tcp --dport 8888 -j DNAT --to-destination 10.0.1.2:8000
-A DOCKER -i docker0 -j RETURNo
# iptables -S -t mangle
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-P POSTROUTING ACCEPT
# iptables -S -t raw
-P PREROUTING ACCEPT
-P OUTPUT ACCEPT
# iptables -S -t security
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
Asked by nicop
(51 rep)
May 15, 2020, 01:47 PM
Last activity: May 18, 2020, 07:41 AM
Last activity: May 18, 2020, 07:41 AM