How to allow ServiceAccount list namespaces it has access to within a cluster?
1
vote
1
answer
6354
views
I have a cluster with multiple namespaces. Let's call them: 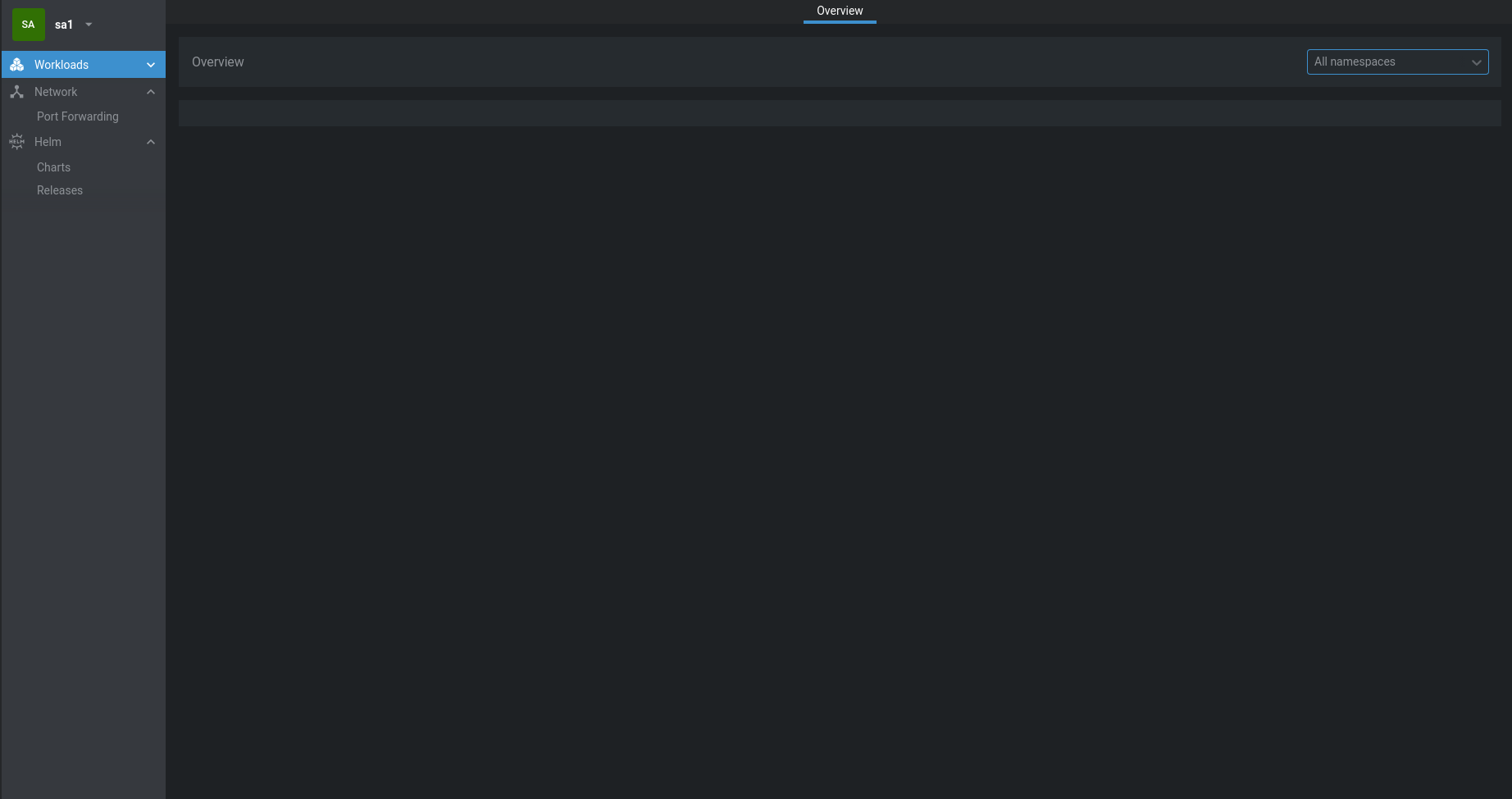 I tried to add namespace the user has in fact access to via
I tried to add namespace the user has in fact access to via 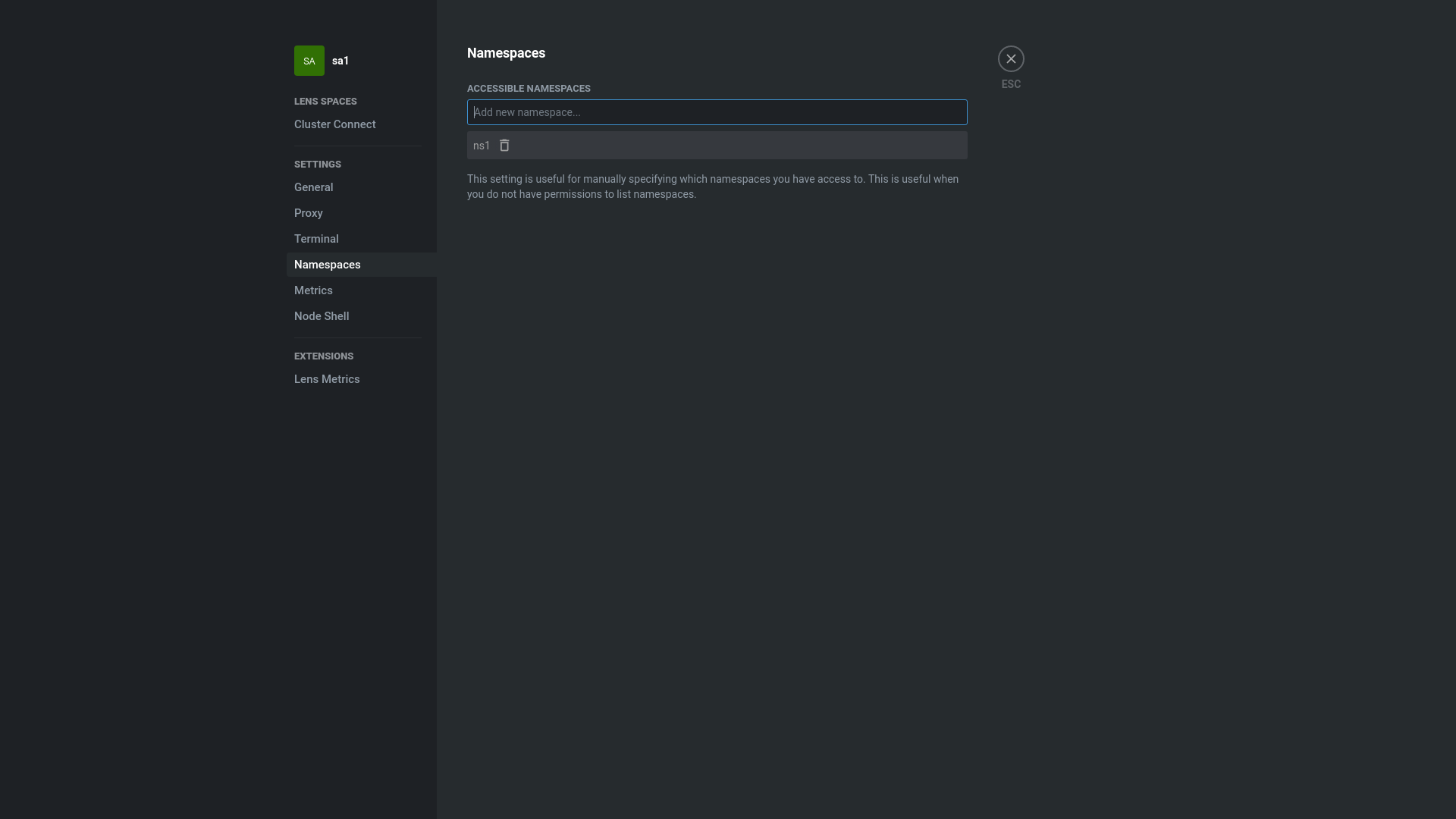 I still don't see anything, only blank dashboards.
I still don't see anything, only blank dashboards.
 ServiceAccount:
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa1
namespace: sa-ns
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa2
namespace: sa-ns
Role:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns1
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns2
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
RoleBinding:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns1
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa1
namespace: sa-ns
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns2
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa2
namespace: sa-ns
I tried to use
ServiceAccount:
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa1
namespace: sa-ns
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa2
namespace: sa-ns
Role:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns1
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns2
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
RoleBinding:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns1
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa1
namespace: sa-ns
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns2
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa2
namespace: sa-ns
I tried to use
ns1 and ns2 I also have multiple service accounts, lets call them sa1 and sa2, all in one namespace - sa-ns.
Both users can access all resources within both namespaces, however they cannot list namespaces they are part of. kubectl get ns --as=sa1 returns:
Error from server (Forbidden): namespaces is forbidden: User "sa1" cannot list resource "namespaces" in API group "" at the cluster scope
It works only if I manually specify which namespace I want to list:
kubectl get ns ns1 --as=sa1
NAME STATUS AGE
ns1 Active 6d6hsa1 and sa2 be able to list all namespaces within cluster they have access to. In this case ns1 and ns2.
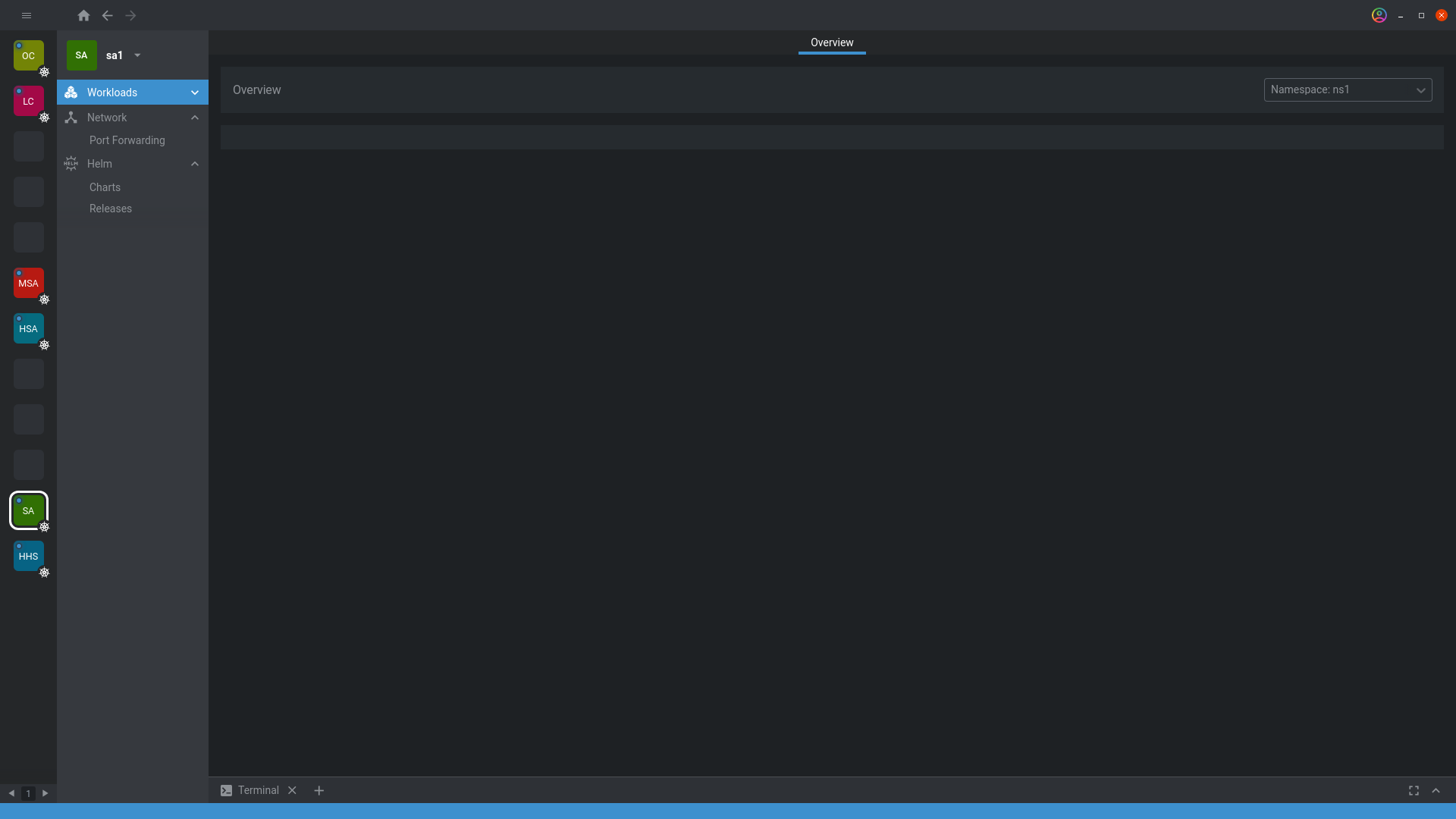
This behavior also probably wont allow me to list namespaces and it's resources in Lens dashboards. From the the namespace list I can list only the namespace sa-ns the users sa1 & sa2 are part of. Dashboards are however empty as you can seen on the image bellow.
 I tried to add namespace the user has in fact access to via
I tried to add namespace the user has in fact access to via ACCESSIBLE NAMESPACES feature in Lens, but it doesn't work either.
 I still don't see anything, only blank dashboards.
I still don't see anything, only blank dashboards.
 ServiceAccount:
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa1
namespace: sa-ns
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa2
namespace: sa-ns
Role:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns1
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns2
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
RoleBinding:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns1
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa1
namespace: sa-ns
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns2
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa2
namespace: sa-ns
I tried to use
ServiceAccount:
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa1
namespace: sa-ns
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: sa2
namespace: sa-ns
Role:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns1
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: admin-role
namespace: ns2
rules:
- apiGroups:
- "*"
resources:
- "*"
verbs:
- "*"
RoleBinding:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns1
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa1
namespace: sa-ns
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: admin-role-binding
namespace: ns2
roleRef:
kind: Role
name: admin-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: sa2
namespace: sa-ns
I tried to use ClusterRoleinstead of Role but nothing has changed.
Asked by JohnyFailLab
(163 rep)
Apr 18, 2022, 06:52 PM
Last activity: Jun 15, 2025, 04:04 PM
Last activity: Jun 15, 2025, 04:04 PM