Ricoh SP200 NW or installing PCL-6 like driver on Sierra
1
vote
0
answers
229
views
Is there any way to make this printer work? A long time ago I made it work it on Ubuntu with PCL-6 driver (I'm not sure about the name), is there similar driver for Sierra?
I already tried IPP with universal PostScript driver but it doesn't work.
Here's 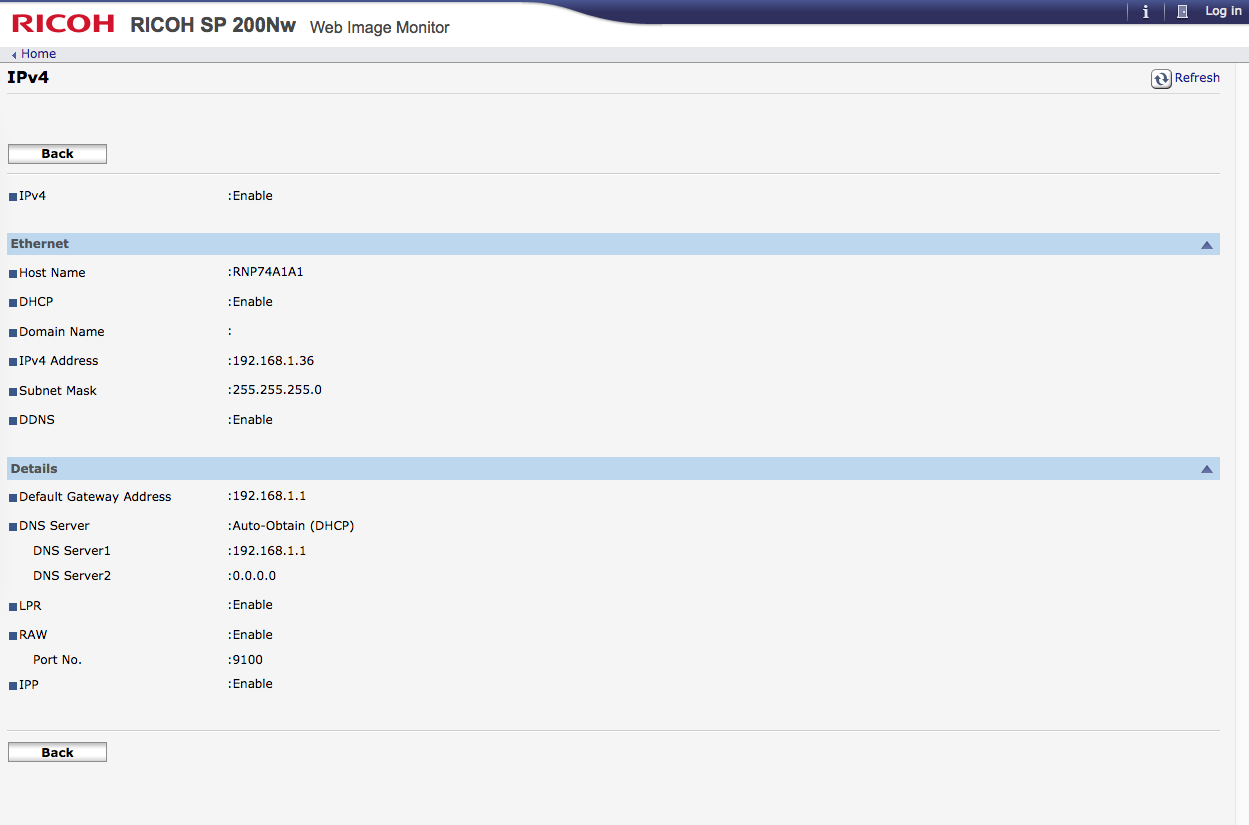
nmap output which may be helpful:
Mys-iMac:~ me$ nmap -v -A 192.168.1.36
Starting Nmap 7.50 ( https://nmap.org ) at 2017-07-02 18:52 MSK
NSE: Loaded 144 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:52
Completed NSE at 18:52, 0.00s elapsed
Initiating NSE at 18:52
Completed NSE at 18:52, 0.00s elapsed
Initiating Ping Scan at 18:52
Scanning 192.168.1.36 [2 ports]
Completed Ping Scan at 18:52, 0.10s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:52
Completed Parallel DNS resolution of 1 host. at 18:52, 0.18s elapsed
Initiating Connect Scan at 18:52
Scanning 192.168.1.36 [1000 ports]
Discovered open port 80/tcp on 192.168.1.36
Discovered open port 2323/tcp on 192.168.1.36
Discovered open port 9100/tcp on 192.168.1.36
Connect Scan Timing: About 47.27% done; ETC: 18:53 (0:00:35 remaining)
Discovered open port 515/tcp on 192.168.1.36
Discovered open port 631/tcp on 192.168.1.36
Completed Connect Scan at 18:53, 65.74s elapsed (1000 total ports)
Initiating Service scan at 18:53
Scanning 4 services on 192.168.1.36
Completed Service scan at 18:54, 90.20s elapsed (5 services on 1 host)
NSE: Script scanning 192.168.1.36.
Initiating NSE at 18:54
Completed NSE at 18:57, 126.78s elapsed
Initiating NSE at 18:57
Completed NSE at 18:57, 8.34s elapsed
Nmap scan report for 192.168.1.36
Host is up (2.3s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http?
515/tcp open printer?
| fingerprint-strings:
| TerminalServer:
|_ Fictive printer queue short information
631/tcp open ipp?
2323/tcp open telnet
| fingerprint-strings:
| GenericLines:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0>
| 192.168.1.36#0>
| 192.168.1.36#0>
| GetRequest:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0> GET / HTTP/1.0
| ipcom_shell : Unknown command: 'GET'.
| 192.168.1.36#0>
| 192.168.1.36#0>
| Help:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0> HELP
| ipcom_shell : Unknown command: 'HELP'.
| 192.168.1.36#0>
| NULL:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0>
| RPCCheck:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0> (r
| [D|(r
| SIPOptions:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0> OPTIONS sip:nm SIP/2.0
| ipcom_shell : Unknown command: 'OPTIONS'.
| 192.168.1.36#0> Via: SIP/2.0/TCP nm;branch=foo
| ipcom_shell : Unknown command: 'Via:'.
| 192.168.1.36#0> From: ;tag=root
| ipcom_shell : Unknown command: 'From:'.
| 192.168.1.36#0> To:
| ipcom_shell : Unknown command: 'To:'.
| 192.168.1.36#0> Call-ID: 50000
| ipcom_shell : Unknown command: 'Call-ID:'.
| 192.168.1.36#0> CSeq: 42 OPTIONS
| ipcom_shell : Unknown command: 'CSeq:'.
| 192.168.1.36#0> Max-Forwards: 70
| ipcom_shell : Unknown command: 'Max-Forwards:'.
| 192.168.1.36#0> Content-Length: 0
| ipcom_shell : Unknown command: 'Content-Length:'.
| 192.168.1.36#0> Contact:
| ipcom_shell : Unknown command: 'Contact:'.
| 192.168.1.36#0> Accept: application/
| tn3270:
| Copyright (c) Interpeak AB 2000-2005. All rights reserved.
| Welcome to IPCOM SHELL. Type help for a list of commands.
| 192.168.1.36#0>
|_ IBM-3279-4-E
5002/tcp filtered rfe
9100/tcp open jetdirect?
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port515-TCP:V=7.50%I=7%D=7/2%Time=59591700%P=x86_64-apple-darwin13.4.0%
SF:r(TerminalServer,29,"Fictive\x20printer\x20queue\x20short\x20informatio
SF:n\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2323-TCP:V=7.50%I=7%D=7/2%Time=595916FF%P=x86_64-apple-darwin13.4.0
SF:%r(NULL,94,"\xff\xfb\x03\xff\xfb\x01\xff\xfd\x1fCopyright\x20\(c\)\x20I
SF:nterpeak\x20AB\x202000-2005\.\x20All\x20rights\x20reserved\.\r\n\r\nWel
SF:come\x20to\x20IPCOM\x20SHELL\.\x20Type\x20help\x20for\x20a\x20list\x20o
SF:f\x20commands\.\r\n\r\n192\.168\.1\.36#0>\x20")%r(tn3270,AF,"\xff\xfb\x
SF:03\xff\xfb\x01\xff\xfd\x1fCopyright\x20\(c\)\x20Interpeak\x20AB\x202000
SF:-2005\.\x20All\x20rights\x20reserved\.\r\n\r\nWelcome\x20to\x20IPCOM\x2
SF:0SHELL\.\x20Type\x20help\x20for\x20a\x20list\x20of\x20commands\.\r\n\r\
SF:n192\.168\.1\.36#0>\x20\xff\xfe\x18\xff\xfe\x19\xff\xfc\x19\xff\xfe\0\x
SF:ff\xfc\0IBM-3279-4-E")%r(GenericLines,B8,"\xff\xfb\x03\xff\xfb\x01\xff\
SF:xfd\x1fCopyright\x20\(c\)\x20Interpeak\x20AB\x202000-2005\.\x20All\x20r
SF:ights\x20reserved\.\r\n\r\nWelcome\x20to\x20IPCOM\x20SHELL\.\x20Type\x2
SF:0help\x20for\x20a\x20list\x20of\x20commands\.\r\n\r\n192\.168\.1\.36#0>
SF:\x20\r\n192\.168\.1\.36#0>\x20\r\n192\.168\.1\.36#0>\x20")%r(GetRequest
SF:,EE,"\xff\xfb\x03\xff\xfb\x01\xff\xfd\x1fCopyright\x20\(c\)\x20Interpea
SF:k\x20AB\x202000-2005\.\x20All\x20rights\x20reserved\.\r\n\r\nWelcome\x2
SF:0to\x20IPCOM\x20SHELL\.\x20Type\x20help\x20for\x20a\x20list\x20of\x20co
SF:mmands\.\r\n\r\n192\.168\.1\.36#0>\x20GET\x20/\x20HTTP/1\.0\r\r\nipcom_
SF:shell\x20:\x20Unknown\x20command:\x20'GET'\.\r\n192\.168\.1\.36#0>\x20\
SF:r\n192\.168\.1\.36#0>\x20")%r(RPCCheck,A5,"\xff\xfb\x03\xff\xfb\x01\xff
SF:\xfd\x1fCopyright\x20\(c\)\x20Interpeak\x20AB\x202000-2005\.\x20All\x20
SF:rights\x20reserved\.\r\n\r\nWelcome\x20to\x20IPCOM\x20SHELL\.\x20Type\x
SF:20help\x20for\x20a\x20list\x20of\x20commands\.\r\n\r\n192\.168\.1\.36#0
SF:>\x20\(r\x1b\[D\x1b\[D\|\(r\x1b\[D\x1b\[D")%r(Help,D2,"\xff\xfb\x03\xff
SF:\xfb\x01\xff\xfd\x1fCopyright\x20\(c\)\x20Interpeak\x20AB\x202000-2005\
SF:.\x20All\x20rights\x20reserved\.\r\n\r\nWelcome\x20to\x20IPCOM\x20SHELL
SF:\.\x20Type\x20help\x20for\x20a\x20list\x20of\x20commands\.\r\n\r\n192\.
SF:168\.1\.36#0>\x20HELP\r\nipcom_shell\x20:\x20Unknown\x20command:\x20'HE
SF:LP'\.\r\n192\.168\.1\.36#0>\x20")%r(SIPOptions,3D6,"\xff\xfb\x03\xff\xf
SF:b\x01\xff\xfd\x1fCopyright\x20\(c\)\x20Interpeak\x20AB\x202000-2005\.\x
SF:20All\x20rights\x20reserved\.\r\n\r\nWelcome\x20to\x20IPCOM\x20SHELL\.\
SF:x20Type\x20help\x20for\x20a\x20list\x20of\x20commands\.\r\n\r\n192\.168
SF:\.1\.36#0>\x20OPTIONS\x20sip:nm\x20SIP/2\.0\r\nipcom_shell\x20:\x20Unkn
SF:own\x20command:\x20'OPTIONS'\.\r\n192\.168\.1\.36#0>\x20Via:\x20SIP/2\.
SF:0/TCP\x20nm;branch=foo\r\nipcom_shell\x20:\x20Unknown\x20command:\x20'V
SF:ia:'\.\r\n192\.168\.1\.36#0>\x20From:\x20;tag=root\r\nipcom_
SF:shell\x20:\x20Unknown\x20command:\x20'From:'\.\r\n192\.168\.1\.36#0>\x2
SF:0To:\x20\r\nipcom_shell\x20:\x20Unknown\x20command:\x20'To
SF::'\.\r\n192\.168\.1\.36#0>\x20Call-ID:\x2050000\r\nipcom_shell\x20:\x20
SF:Unknown\x20command:\x20'Call-ID:'\.\r\n192\.168\.1\.36#0>\x20CSeq:\x204
SF:2\x20OPTIONS\r\nipcom_shell\x20:\x20Unknown\x20command:\x20'CSeq:'\.\r\
SF:n192\.168\.1\.36#0>\x20Max-Forwards:\x2070\r\nipcom_shell\x20:\x20Unkno
SF:wn\x20command:\x20'Max-Forwards:'\.\r\n192\.168\.1\.36#0>\x20Content-Le
SF:ngth:\x200\r\nipcom_shell\x20:\x20Unknown\x20command:\x20'Content-Lengt
SF:h:'\.\r\n192\.168\.1\.36#0>\x20Contact:\x20\r\nipcom_shell\x
SF:20:\x20Unknown\x20command:\x20'Contact:'\.\r\n192\.168\.1\.36#0>\x20Acc
SF:ept:\x20application/");
NSE: Script Post-scanning.
Initiating NSE at 18:57
Completed NSE at 18:57, 0.00s elapsed
Initiating NSE at 18:57
Completed NSE at 18:57, 0.00s elapsed
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 292.69 seconds
Printer dashboard:

Asked by blits
(111 rep)
Jul 2, 2017, 04:49 PM
Last activity: Jul 6, 2017, 10:10 AM
Last activity: Jul 6, 2017, 10:10 AM