How can I verify little snitch warnings on SSH processes?
12
votes
3
answers
900
views
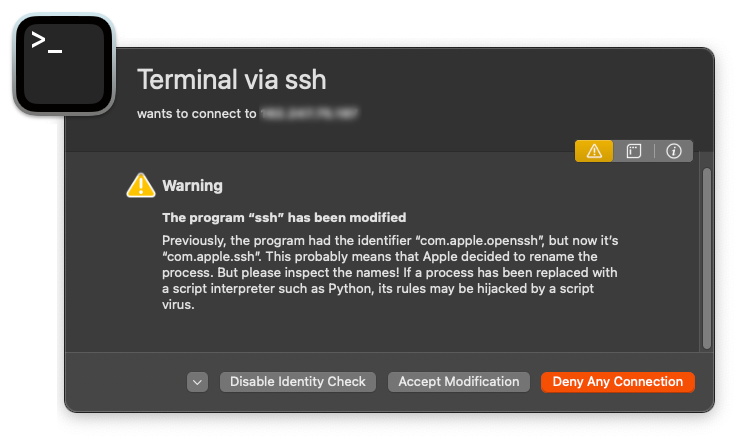
It's been a while since I've needed to connect to a server via SSH. When I tried to connect today, Little Snitch gave me this warning:
> The program "ssh" has been modified
>
> Previously, the program had the identifier "com.apple.openssh", but
> now it's "com.apple.ssh". This probably means that Apple decided to
> rename the process. But please inspect the names! If a process has
> been replaced with a script interpreter such as Python, its rules may
> be hijacked by a script virus.
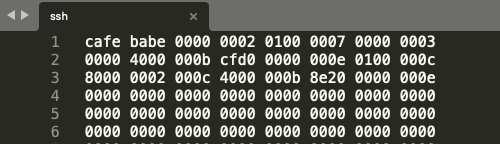
 And this is probably nothing, but looking at the binary in a code editor, I noticed the first 8 characters say "cafe babe". Strange, right?
And this is probably nothing, but looking at the binary in a code editor, I noticed the first 8 characters say "cafe babe". Strange, right?
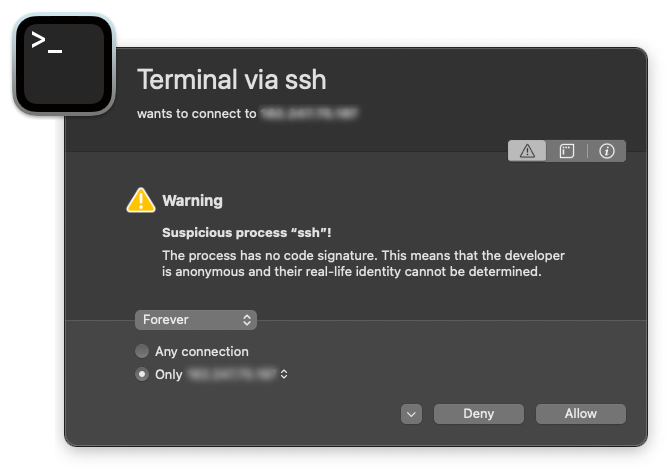
 I couldn't find any info about it online, so I installed openssh via Homebrew. But when I run that, Little Snitch warns that the process has no signature.
I couldn't find any info about it online, so I installed openssh via Homebrew. But when I run that, Little Snitch warns that the process has no signature.
 Anyway, I checked the signature on the Apple binary using
Anyway, I checked the signature on the Apple binary using
 And this is probably nothing, but looking at the binary in a code editor, I noticed the first 8 characters say "cafe babe". Strange, right?
And this is probably nothing, but looking at the binary in a code editor, I noticed the first 8 characters say "cafe babe". Strange, right?
 I couldn't find any info about it online, so I installed openssh via Homebrew. But when I run that, Little Snitch warns that the process has no signature.
I couldn't find any info about it online, so I installed openssh via Homebrew. But when I run that, Little Snitch warns that the process has no signature.
 Anyway, I checked the signature on the Apple binary using
Anyway, I checked the signature on the Apple binary using codesign -db --verbose=4 /usr/bin/ssh, but I can't find anything online to compare the output against.
**So how can I be sure this binary is legit before allowing it to connect?**
BTW, I'm running Ventura 13.1.
Edit: Here's the output of codesign -dv --verbose=4 /usr/bin/ssh:
Executable=/usr/bin/ssh
Identifier=com.apple.ssh
Format=Mach-O universal (x86_64 arm64e)
CodeDirectory v=20400 size=6182 flags=0x0(none) hashes=183+7 location=embedded
Platform identifier=14
VersionPlatform=1
VersionMin=852224
VersionSDK=852224
Hash type=sha256 size=32
CandidateCDHash sha256=d19d6f7a19eb7178c68fc67c197bc8d8fbeda7e7
CandidateCDHashFull sha256=d19d6f7a19eb7178c68fc67c197bc8d8fbeda7e791bd5a9e96f67e9b2169eb16
Hash choices=sha256
CMSDigest=d19d6f7a19eb7178c68fc67c197bc8d8fbeda7e791bd5a9e96f67e9b2169eb16
CMSDigestType=2
Executable Segment base=0
Executable Segment limit=671744
Executable Segment flags=0x1
Page size=4096
Launch Constraints:
None
CDHash=d19d6f7a19eb7178c68fc67c197bc8d8fbeda7e7
Signature size=4442
Authority=Software Signing
Authority=Apple Code Signing Certification Authority
Authority=Apple Root CA
Signed Time=Nov 5, 2022 at 12:44:29 AM
Info.plist=not bound
TeamIdentifier=not set
Sealed Resources=none
Internal requirements count=1 size=64
Output of 'uname -a':
Darwin MacBook-Pro.local 22.2.0 Darwin Kernel Version 22.2.0: Fri Nov 11 02:08:47 PST 2022; root:xnu-8792.61.2~4/RELEASE_X86_64 x86_64
Asked by thingEvery
(223 rep)
Jan 20, 2023, 06:09 AM
Last activity: Apr 3, 2024, 06:30 PM
Last activity: Apr 3, 2024, 06:30 PM