Signal is disclosing peer-to-peer communication not sent through its own VPN to Google, or meta data thereof (i.e. call & duration, aliases & numbers)
0
votes
0
answers
101
views
**Premise**
Signal is disclosing peer-to-peer communication not sent through its own VPN to Google, or meta data thereof (i.e. call & duration, aliases & numbers) covertly, and without explicit disclosure of this fact in its ToS/EULA etc.. (Please see the attached screenshot below)[\[1\]]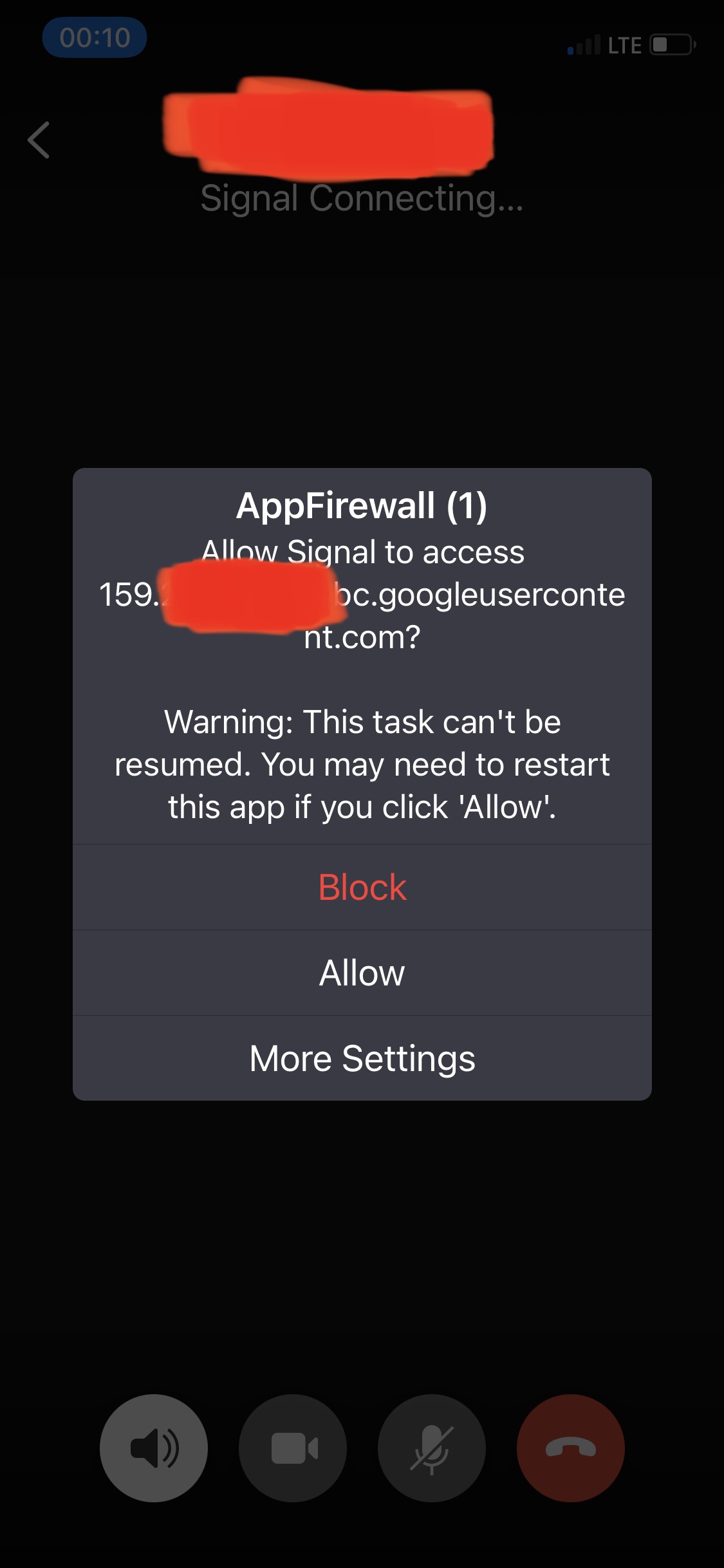 2
I have learned about this during research with a jailbroken iPhone running iOS 14.3, and AppFirewall[\[3\]][3] [\[4\]][4] , a jailbreak tweak for iOS.
**Question**
Is there any other way to block this without having to jailbreak an iPhone, and having a non-OEM system-wide, app-to-app firewall system set up?
**Depction**
2
I have learned about this during research with a jailbroken iPhone running iOS 14.3, and AppFirewall[\[3\]][3] [\[4\]][4] , a jailbreak tweak for iOS.
**Question**
Is there any other way to block this without having to jailbreak an iPhone, and having a non-OEM system-wide, app-to-app firewall system set up?
**Depction**
 -----------
**Footnotes**
2: Transcript of image: [signal indicator at 1 out of 4 bars; "LTE", ¶, Contact name or number redacted in red ¶] "Signal Connecting... [¶] AppFirewall (1) [¶] Allow Signal to access [¶] 159.***.***.***.bc.googleusercontent.com? [¶] Warning: This task can't be resumed. You may need to restart this app if you click 'Allow'. [¶] Block[,¶] Allow[,¶ or] More Settings"
3: https://github.com/doug-leith/appFirewall
4: https://www.ios-repo-updates.com/repository/bigboss/package/ca.btraas.appfirewall
-----------
**Footnotes**
2: Transcript of image: [signal indicator at 1 out of 4 bars; "LTE", ¶, Contact name or number redacted in red ¶] "Signal Connecting... [¶] AppFirewall (1) [¶] Allow Signal to access [¶] 159.***.***.***.bc.googleusercontent.com? [¶] Warning: This task can't be resumed. You may need to restart this app if you click 'Allow'. [¶] Block[,¶] Allow[,¶ or] More Settings"
3: https://github.com/doug-leith/appFirewall
4: https://www.ios-repo-updates.com/repository/bigboss/package/ca.btraas.appfirewall
 2
I have learned about this during research with a jailbroken iPhone running iOS 14.3, and AppFirewall[\[3\]][3] [\[4\]][4] , a jailbreak tweak for iOS.
**Question**
Is there any other way to block this without having to jailbreak an iPhone, and having a non-OEM system-wide, app-to-app firewall system set up?
**Depction**
2
I have learned about this during research with a jailbroken iPhone running iOS 14.3, and AppFirewall[\[3\]][3] [\[4\]][4] , a jailbreak tweak for iOS.
**Question**
Is there any other way to block this without having to jailbreak an iPhone, and having a non-OEM system-wide, app-to-app firewall system set up?
**Depction**
 -----------
**Footnotes**
2: Transcript of image: [signal indicator at 1 out of 4 bars; "LTE", ¶, Contact name or number redacted in red ¶] "Signal Connecting... [¶] AppFirewall (1) [¶] Allow Signal to access [¶] 159.***.***.***.bc.googleusercontent.com? [¶] Warning: This task can't be resumed. You may need to restart this app if you click 'Allow'. [¶] Block[,¶] Allow[,¶ or] More Settings"
3: https://github.com/doug-leith/appFirewall
4: https://www.ios-repo-updates.com/repository/bigboss/package/ca.btraas.appfirewall
-----------
**Footnotes**
2: Transcript of image: [signal indicator at 1 out of 4 bars; "LTE", ¶, Contact name or number redacted in red ¶] "Signal Connecting... [¶] AppFirewall (1) [¶] Allow Signal to access [¶] 159.***.***.***.bc.googleusercontent.com? [¶] Warning: This task can't be resumed. You may need to restart this app if you click 'Allow'. [¶] Block[,¶] Allow[,¶ or] More Settings"
3: https://github.com/doug-leith/appFirewall
4: https://www.ios-repo-updates.com/repository/bigboss/package/ca.btraas.appfirewall
Asked by Raiden Snaker
(15 rep)
May 16, 2023, 08:00 AM