Ask Different (Apple)
Q&A for power users of Apple hardware and software
Latest Questions
4
votes
4
answers
1179
views
Want to remove filevault prompt on shutdown/reboot
Whenever I'm logged in as a certain user and trigger a shutdown or restart, I get prompted to enable FileVault. - I have searched everywhere to find the hook that causes this prompt, but I can't find it. - I've searched all the LaunchDaemon and LaunchAgent directories I can find. - I've reviewed the...
Whenever I'm logged in as a certain user and trigger a shutdown or restart, I get prompted to enable FileVault.
- I have searched everywhere to find the hook that causes this prompt, but I can't find it.
- I've searched all the LaunchDaemon and LaunchAgent directories I can find.
- I've reviewed the output of launchctl find.
- I've done other things in the past as well but I don't remember them all.
- I have upgraded my computer and transferred my user account multiple times since this started happening. It seems to stick to my user account.
- I believe this might have come from Symantec Endpoint Encryption that was installed by my employer many years ago. But I've also tried all the uninstaller techniques I can find for that.
It appears after all the desktop stuff has gone away.
Any ideas for where else I can look for a hook that might trigger this?
Update: **FileVault** is not currently enabled on the disk and I do not want to enable it.
![Screenshot of the FileVault dialog box saying 'To add this user to FileVault, enter the password for 'cquenell.'' ][1]
Chris Quenelle
(984 rep)
Oct 9, 2021, 06:50 PM
• Last activity: Aug 2, 2025, 04:56 PM
3
votes
1
answers
581
views
How to clone HDD to SSD with FileVault enabled?
I use an Apple MacBook Pro 13'' mid-2012 with a **1 TB HDD**. FileVault is enabled so the **disk is encrypted**. I'm using macOS Mojave 10.14.6. I purchased an **1 TB SSD** (Crucial MX 500, CT1000MX500SSD1). I want to **clone from the HDD to the SSD**, in order to transfer the data and the OS in the...
I use an Apple MacBook Pro 13'' mid-2012 with a **1 TB HDD**. FileVault is enabled so the **disk is encrypted**. I'm using macOS Mojave 10.14.6.
I purchased an **1 TB SSD** (Crucial MX 500, CT1000MX500SSD1). I want to **clone from the HDD to the SSD**, in order to transfer the data and the OS in their current state.
I want to avoid using a third-party software, so I tried to use **Disk Utility** with the "restore" feature.
How should I proceed? How should I format the SSD before?
I tried formatting the SSD under APFS. Then I launched a restore operation from my HDD (internal) to SSD (external). But it consistently fails with *"OSStatus error 28"*, saying *"could not restore - no free space on the device"*, *"the operation could not be completed"*, *"the operation failed"*, *"the destination does not have enough space"*.
 I don't understand because both disks are supposed to have the same capacity.
I don't understand because both disks are supposed to have the same capacity.


 I don't understand because both disks are supposed to have the same capacity.
I don't understand because both disks are supposed to have the same capacity.


Croal
(53 rep)
Sep 28, 2021, 09:55 PM
• Last activity: Jun 10, 2025, 12:07 PM
2
votes
1
answers
301
views
Old iMac Hard Drive not readable as external
My friend's iMac would not boot. I ran TechTool Protogo using a thumb drive with TTP 9 to test the hard drive. It reported several hundred failed sectors on the drive, so I recommended we replace it. Before replacing the hard drive in the iMac, I booted off an old hard drive from an old laptop using...
My friend's iMac would not boot. I ran TechTool Protogo using a thumb drive with TTP 9 to test the hard drive. It reported several hundred failed sectors on the drive, so I recommended we replace it.
Before replacing the hard drive in the iMac, I booted off an old hard drive from an old laptop using a USB to SATA adapter to make sure the iMac would boot off another drive, in other words, I wanted to make sure the problem was in fact the hard drive. It booted fine, although I could not access the damaged internal drive as it was encrypted with FileVault.
I went ahead and completed the hard drive replacement, putting in an SSD and connecting the damaged internal to my USB to SATA adapter. I expected I could get the password for the old hard drive later to copy any data I could save from it.
I used internet recovery to install the original OS that came on the iMac to the new SSD, and then upgraded to High Sierra, which is what my friend originally had on it. The iMac now boots fine.
The problem I have is the former internal drive will not mount using the USB to SATA adapter, rather the iMac reports it is unreadable. I also used the adapter to try and mount the hard drive on a MacBook Pro, but got the same warning,
Is there something related to FileVault that would prevent this drive from working outside the iMac? I had researched this earlier, and thought I was okay. Any advice or help would be greatly appreciated.
1. iMac Model: 21.5-inch, Late 2013
2. OS installed on failed disk... High Sierra
3. OS installed on new SSD ... High Sierra
4. OS installed on MacBook Pro ... Mojave
I did find a thread on here with a similar problem and tried fixing it with GPT commands in terminal. I wonder if I have made it worse...
Please help me. I really wanted to help my friend and though I got her iMac up and running, I really, really want to help her get files back.
------- Additional Information -------
The drive is a HGST SATA drive, model 5K1000-1000.
The USB to SATA adapter is the CablesToGo #3050.
@benwiggy, When I booted from the laptop HDD, the iMac started up fine. A window appeared and I believe it said the internal drive was encrypted and asked for its password. I simply ignored it assuming I could access it later as an external drive and get the same prompt. When I tried to access it as an external drive, it said it was not readable and offered me the option to ignore, eject, or initialize. I chose ignore.
**Terminal Commands and the results:**
Bobs-MBP:~ bob$ sudo gpt -r show disk2
start size index contents
0 1 PMBR
1 1 Pri GPT header
2 4 Pri GPT table
6 244190635
244190641 4 Sec GPT table
244190645 1 Sec GPT header
Bobs-MBP:~ bob$ diskutil list
/dev/disk2 (external, physical):
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *1.0 TB disk2
RoboMo
(21 rep)
Jan 29, 2021, 02:55 PM
• Last activity: Jun 8, 2025, 02:04 PM
10
votes
2
answers
6600
views
How can I tell whether or not my FileVault recovery key is stored in iCloud?
I setup FileVault on my MacBook years ago. I believe I set things up so that my recovery key is stored in iCloud, but I'm not sure. And the FileVault preferences pane doesn't give any clues. [![FileVault Preferences Pane][1]][1] How can I check whether or not my FileVault recovery key is stored in i...
I setup FileVault on my MacBook years ago. I believe I set things up so that my recovery key is stored in iCloud, but I'm not sure. And the FileVault preferences pane doesn't give any clues.
 How can I check whether or not my FileVault recovery key is stored in iCloud?
How can I check whether or not my FileVault recovery key is stored in iCloud?
 How can I check whether or not my FileVault recovery key is stored in iCloud?
How can I check whether or not my FileVault recovery key is stored in iCloud?
Nick Chammas
(567 rep)
Mar 1, 2019, 09:34 PM
• Last activity: Jun 6, 2025, 02:49 PM
5
votes
2
answers
644
views
How to remotely connect to a Mac with FileVault where the OS does not start until a user account logs in?
I have a Mac Mini, M1, which I use remotely via SSH / VNC. From time to time I need to issues a reboot to the machine. After rebooting however, I am unable to establish an SSH connection as all I get are 'Connection Refused' packets. It seems that machine does not actually finish the boot process un...
I have a Mac Mini, M1, which I use remotely via SSH / VNC.
From time to time I need to issues a reboot to the machine.
After rebooting however, I am unable to establish an SSH connection as all I get are 'Connection Refused' packets.
It seems that machine does not actually finish the boot process until first login; only after entering my password on the local machine does it start accepting SSH connections.
How can I make the Mac actually finish booting without someone physically at the machine?
Matt Clark
(422 rep)
Aug 24, 2021, 03:52 AM
• Last activity: Jun 5, 2025, 01:48 AM
0
votes
1
answers
870
views
macbook air keeps restarting bc of a problem (filevault decrypting is stuck in 99)
I turned my FileVault off (yes big mistake) without researching anything. I don't know what made me turn it off brain fart or curiosity maybe. t was all okay until the decryption reached 99% when I plug in my laptop to the charger, My laptop restarts on its own, is it supposed to do that? The batter...
I turned my FileVault off (yes big mistake) without researching anything. I don't know what made me turn it off brain fart or curiosity maybe.
t was all okay until the decryption reached 99% when I plug in my laptop to the charger, My laptop restarts on its own, is it supposed to do that?
The battery drains fast when I try to use my laptop (charger unplugged).
I have tried disabling and enabling it from terminal but it ends up only showing this
$ sudo fdesetup disable
Password:
Enter the user name://
Enter the password for user '//':
FileVault was not disabled (2).
$ fdesetup status
FileVault is On.
Decryption in progress: Percent completed = 99
yori
(1 rep)
Jul 13, 2022, 05:16 AM
• Last activity: Jun 2, 2025, 01:07 AM
4
votes
1
answers
798
views
Manually Decrypt Partially Cloned APFS Volume
I recently attempted to clone a failing external drive to a new external drive. The clone failed part-way into the process. The original drive hardware has now fully failed, so I'm trying to recover as much as I can from the clone. When I plug in the clone, macOS gives me an error reading "The disk...
I recently attempted to clone a failing external drive to a new external drive. The clone failed part-way into the process. The original drive hardware has now fully failed, so I'm trying to recover as much as I can from the clone.
When I plug in the clone, macOS gives me an error reading "The disk 'Volume_Name' can't be unlocked. A problem was detected with the disk that prevents it from being unlocked." Disk Utility shows 1.6 TB used. I tried unlocking it from the command line and the Terminal output was  I believe I've recovered the clone volume's cryptouser string from Keychain Access on two separate Macs (they match), so I have both the user and the passphrase. Is there a way to enter these manually and decrypt the drive? Either via the Terminal or a third-party piece of software?
For reference, I got a lot of information from this page even though it outlines boot drives instead of external ones.
Thank you in advance!
I believe I've recovered the clone volume's cryptouser string from Keychain Access on two separate Macs (they match), so I have both the user and the passphrase. Is there a way to enter these manually and decrypt the drive? Either via the Terminal or a third-party piece of software?
For reference, I got a lot of information from this page even though it outlines boot drives instead of external ones.
Thank you in advance!
Passphrase incorrect or user does not exist. I am certain I'm entering the passphrase correctly.
A scan in Data Rescue shows a recognizable list of files and folders. I can copy a file from the clone, but I can't open it. I am guessing that the files are encrypted individually while the folder structure is not.
From my research, macOS creates a separate cryptouser on an encrypted disk (separate from a Mac account/user) so that one password can open the disk on any Mac. When I used diskutil apfs listcryptousers /dev/Volume_Name in Terminal, the output is No cryptographic users for Volume_Name when it *should* output something like this:
 I believe I've recovered the clone volume's cryptouser string from Keychain Access on two separate Macs (they match), so I have both the user and the passphrase. Is there a way to enter these manually and decrypt the drive? Either via the Terminal or a third-party piece of software?
For reference, I got a lot of information from this page even though it outlines boot drives instead of external ones.
Thank you in advance!
I believe I've recovered the clone volume's cryptouser string from Keychain Access on two separate Macs (they match), so I have both the user and the passphrase. Is there a way to enter these manually and decrypt the drive? Either via the Terminal or a third-party piece of software?
For reference, I got a lot of information from this page even though it outlines boot drives instead of external ones.
Thank you in advance!
jay-z
(41 rep)
May 8, 2022, 08:38 PM
• Last activity: May 30, 2025, 06:10 PM
4
votes
1
answers
3134
views
Make FileVault password different from user login password?
In macOS Catalina, I want to specifically set a different (and longer) password for unlocking FileVault (e.g. when I first turn my MacBook Pro on) vs. a shorter password to use in more casual contexts like unlocking after sleep or when prompted for the admin user password. Is this possible? Usually,...
In macOS Catalina, I want to specifically set a different (and longer) password for unlocking FileVault (e.g. when I first turn my MacBook Pro on) vs. a shorter password to use in more casual contexts like unlocking after sleep or when prompted for the admin user password.
Is this possible?
Usually, people have wanted the opposite . But in Catalina I've tried changing it to be different in both
System Preferences > Users & Groups > Change Password... and System Preferences > Security & Privacy > Change Password... and it makes them both sync up in either case.
I remember in older versions of macOS I would have to enter a different password for FileVault vs. your user password (if they were different). I'm wanting this distinction back.
My user account is the default and only administrator in the system.
Is there a Terminal command to specify user password as distinct from FileVault password?
user163629
Nov 18, 2020, 02:52 PM
• Last activity: Apr 13, 2025, 07:04 PM
3
votes
2
answers
230
views
Hardware-independent recovery key similar to Bitlocker?
I've been doing a bit of research about FileVault and APFS recently, but it still confuses me. I learned about the two types of recovery keys for FileVault, personal recovery key and institutional recovery key. According to what I read, the personal one only works on the same device (if the Mac is b...
I've been doing a bit of research about FileVault and APFS recently, but it still confuses me. I learned about the two types of recovery keys for FileVault, personal recovery key and institutional recovery key. According to what I read, the personal one only works on the same device (if the Mac is broken, access will be impossible) and the institutional one requires an MDM, a PKI, and needs to be configured before the volume is encrypted.
Is there any device-independent recovery key that I can export from an unlocked volume and use for unlocking on any device?
Windows Bitlocker has this function and it is very handy, because in many situation you do not have to mess around with protectors or cryptousers, TPM/T2-chips and similar device-specific mechanisms. One basically exports the AES-key of the drive or something fully equivalent.
I read about a "secure token" but I did not really understand it. Could this be what I am thinking about?
dsfsdfdsf23
(31 rep)
Jun 24, 2021, 02:39 PM
• Last activity: Apr 6, 2025, 02:23 PM
0
votes
0
answers
18
views
Any option to update remotely with FileVault on?
So, after update FileVault will be locked. Previously on Sonoma and earlier I can start update from Preferences.app and rebooted via `sudo fdesetup authrestart` to unlock FileVault after reboot. Now this trick doesn't work, it just reboots without applying the update.
So, after update FileVault will be locked.
Previously on Sonoma and earlier I can start update from Preferences.app and rebooted via
sudo fdesetup authrestart to unlock FileVault after reboot.
Now this trick doesn't work, it just reboots without applying the update.
Egor Egorov
(191 rep)
Mar 14, 2025, 04:36 AM
7
votes
3
answers
3152
views
Error recovering MacBook login password: “There was an error communicating with iCloud”
I forgot my Apple MacBook Pro M2 password yesterday (running on MacOS Sonama) and after multiple tries, I tried to recover using recovery options provided by apple. After following all the steps loging in using my Apple ID. In the reset password process, after I logged in using my Apple ID, it sudde...
I forgot my Apple MacBook Pro M2 password yesterday (running on MacOS Sonama) and after multiple tries, I tried to recover using recovery options provided by apple. After following all the steps loging in using my Apple ID.
In the reset password process, after I logged in using my Apple ID, it suddenly shows error “There was an error communicating with iCloud”. It happens right after the step where it tries to load FileVault recovery key.
I do have my FileVault recovery key and have all other passwords.
After contacting with Apple support and have a long conversation and they re-tried all the steps, they simply said: “well, you can only remove everything in your mac, we can’t help you more”
I even tried doing it using the terminal, and I can see a bunch of error printing in the terminal. Here I attached screenshot:

 Error above clearly indicates:
NSSoftLinking - The Shortcut framework’s library couldn’t be loaded from (null).
The function ‘SCTInitShortcut’ can’t be found in the Shortcut framework.
AOSKit: ERROR: CFBundleCreate failed (AppleAccount)
ERROR: Failed to load AppleAccount
and continues:
Missing ep for BTMM
Any idea? It seems I can’t try more passwords as when I try to enter new passwords it says “Account is locked”.
I can’t simply lose my data, it’s my PhD work/codes, and I don’t have backup. Can I do anything with the FileVault recovery key that I have? I don’t mind reinstall everything, but even reinstalling asks for password, which now seems locked.
Error above clearly indicates:
NSSoftLinking - The Shortcut framework’s library couldn’t be loaded from (null).
The function ‘SCTInitShortcut’ can’t be found in the Shortcut framework.
AOSKit: ERROR: CFBundleCreate failed (AppleAccount)
ERROR: Failed to load AppleAccount
and continues:
Missing ep for BTMM
Any idea? It seems I can’t try more passwords as when I try to enter new passwords it says “Account is locked”.
I can’t simply lose my data, it’s my PhD work/codes, and I don’t have backup. Can I do anything with the FileVault recovery key that I have? I don’t mind reinstall everything, but even reinstalling asks for password, which now seems locked.

 Error above clearly indicates:
NSSoftLinking - The Shortcut framework’s library couldn’t be loaded from (null).
The function ‘SCTInitShortcut’ can’t be found in the Shortcut framework.
AOSKit: ERROR: CFBundleCreate failed (AppleAccount)
ERROR: Failed to load AppleAccount
and continues:
Missing ep for BTMM
Any idea? It seems I can’t try more passwords as when I try to enter new passwords it says “Account is locked”.
I can’t simply lose my data, it’s my PhD work/codes, and I don’t have backup. Can I do anything with the FileVault recovery key that I have? I don’t mind reinstall everything, but even reinstalling asks for password, which now seems locked.
Error above clearly indicates:
NSSoftLinking - The Shortcut framework’s library couldn’t be loaded from (null).
The function ‘SCTInitShortcut’ can’t be found in the Shortcut framework.
AOSKit: ERROR: CFBundleCreate failed (AppleAccount)
ERROR: Failed to load AppleAccount
and continues:
Missing ep for BTMM
Any idea? It seems I can’t try more passwords as when I try to enter new passwords it says “Account is locked”.
I can’t simply lose my data, it’s my PhD work/codes, and I don’t have backup. Can I do anything with the FileVault recovery key that I have? I don’t mind reinstall everything, but even reinstalling asks for password, which now seems locked.
Michel Gokan Khan
(281 rep)
Feb 10, 2024, 03:03 PM
• Last activity: Mar 2, 2025, 11:44 AM
0
votes
0
answers
34
views
Login Items (apps) residing on other macOS volume don't autostart on login
I have both Sequoia and Ventura installed in the same APFS container. Ventura uses FileVault. When I add apps from `/Volumes/Ventura/Applications` to Sequoia's Login Items they will not start upon login, but I can double-click them in the Login Items list to start them. I'm not asked to mount any vo...
I have both Sequoia and Ventura installed in the same APFS container. Ventura uses FileVault. When I add apps from
/Volumes/Ventura/Applications to Sequoia's Login Items they will not start upon login, but I can double-click them in the Login Items list to start them. I'm not asked to mount any volumes or prompted for any encryption passwords when doing so, so I assume everything is set up for this to work seamlessly.
What's required in this situation for these Login Items to autostart?
I have five of these Login Items currently and all behave this way.
- Cross-volume shortcuts residing in /Applications also don't work
- Only actual .apps in /Applications seem to work
- Logging out and in again after initial boot will autostart all directly and indirectly referenced cross-volume items
- I don't want to duplicate apps across volumes
Andreas
(2269 rep)
Feb 14, 2025, 06:29 PM
• Last activity: Feb 14, 2025, 06:37 PM
12
votes
3
answers
1427
views
When does encryption actually happen in MacOS/OS X encrypted volumes?
I've noticed a sort-of lazy/post encryption strategy in MacOS/OS X with FileVault enabled and in encrypted Time Machine backups, and I'm curious when actual encryption happens. - When I copy videos from unencrypted external USB 3 volumes to my FileVault encrypted volume, my write speeds are 100+MB/s...
I've noticed a sort-of lazy/post encryption strategy in MacOS/OS X with FileVault enabled and in encrypted Time Machine backups, and I'm curious when actual encryption happens.
- When I copy videos from unencrypted external USB 3 volumes to my FileVault encrypted volume, my write speeds are 100+MB/s. However, I don't think my macbook (Intel Core i7-4980) is capable of encrypting that fast on-the-fly.
- When I complete a time machine backup, a lengthy "encrypting..." step happens, but continues seamlessly after un-mounting/re-mounting. This is more obvious when encryption is happening, but is the data exposed until encryption is complete?
**When does the actual encryption happen? Is there a period of time where my files are vulnerable unencrypted?**
Josh Hibschman
(1294 rep)
Mar 14, 2017, 04:46 PM
• Last activity: Feb 11, 2025, 12:33 PM
0
votes
0
answers
32
views
Retrieving encrypted Mac OS Journaled disk?
I have a problem which I think is unsolvable, however from related posts it does seem like there might be a remote chance... My situation: I keep a regular Time Machine archive backed up to five external drives, 1, 2 and 3 are identical Seagate 2TB drives and also contain around 700gb of identical s...
I have a problem which I think is unsolvable, however from related posts it does seem like there might be a remote chance... My situation:
I keep a regular Time Machine archive backed up to five external drives, 1, 2 and 3 are identical Seagate 2TB drives and also contain around 700gb of identical static data (work and documents amassed over the last 30 or so years that is not needed day to day)
Drives 4 & 5 are 1TB and contain just the daily working Time Machine archive. All disks were created through Disk Utility and formatted to Encrypted Mac OS Extended and all share the same encryption key (This has been performed on 10.13 if that has any bearing)
For complex reasons, drives 1, 2, & 3 have all been erased via Disk Utility to non-encrypted Mac OS Extended (Journaled) The erase process on each disk took a few seconds so I am confident that the encrypted data is still physically on the disk.
After this happened the disks were unplugged and no further data written to them. If it has any bearing, the erase operation happened on 12.4 (Monterey)
Guess what, that 700gb of static data was only stored on those 3 disks, and I need it back.
From my limited understanding of the situation it is almost certainly unsalvageable, however one does live in hope so I wanted to see if there was any approach I could try?
I am reasonably computer literate, but this is a new area for me. Is my only option to perform recovery work on the actual disk or should I try making a disk image via something like dd? (I've never done this before so have no idea if its a literal block for block copy of the entire disk)
This is the output of gpt on one of the three disks that were wiped (all give an identical output):
/dev/disk2 (external, physical):
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *2.0 TB disk2
1: EFI EFI 209.7 MB disk2s1
2: Apple_HFS backup03 2.0 TB disk2s2
start size index contents
0 1 PMBR
1 1 Pri GPT header
2 32 Pri GPT table
34 6
40 409600 1 GPT part - C12A7328-F81F-11D2-BA4B-00A0C93EC93B
409640 3906357344 2 GPT part - 48465300-0000-11AA-AA11-00306543ECAC
3906766984 262150
3907029134 32 Sec GPT table
3907029166 1 Sec GPT header
Am I being naive to think that by remaking index 2 to be type 53746F72-6167-11AA-AA11-00306543ECAC (Core Storage container, including HFS+ FileVault)
and by creating a third index of type 426F6F74-0000-11AA-AA11-00306543ECAC (recovery partition) between blocks 3906766984 and 3907029133 (so size 262150) I might stand a chance?
Or is there some data associated with File Vault operation that is stored in another part of the disk which may have been deleted in the erase operation?
What I think the disk looked like prior to the erase:
/dev/disk2 (external, physical):
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *2.0 TB disk2
1: EFI EFI 209.7 MB disk2s1
2: Apple_HFS backup03 2.0 TB disk2s2
start size index contents
0 1 PMBR
1 1 Pri GPT header
2 32 Pri GPT table
34 6
40 409600 1 GPT part - C12A7328-F81F-11D2-BA4B-00A0C93EC93B
409640 3906357344 2 GPT part - 53746F72-6167-11AA-AA11-00306543ECAC
3906766984 262150 3 GPT part - 426F6F74-0000-11AA-AA11-00306543ECAC
3907029134 32 Sec GPT table
3907029166 1 Sec GPT header
Apologies for the formatting of the disk info data, any help or guidance would be greatly appreciated!
UncleIra
(1 rep)
Feb 6, 2025, 06:43 PM
2
votes
3
answers
376
views
How can I cold-boot a mac with FileVault enabled without physical access to the mac?
If I had a Linux machine, I'd be able to enter the password for the encrypted boot disk in a serial terminal during the boot process, via another machine connected to the serial port I can SSH into. Is there a way I can do this with macOS as well? Or is there maybe another setup that allows me to un...
If I had a Linux machine, I'd be able to enter the password for the encrypted boot disk in a serial terminal during the boot process, via another machine connected to the serial port I can SSH into.
Is there a way I can do this with macOS as well?
Or is there maybe another setup that allows me to unlock FileVault during boot remotely?
damiano
(41 rep)
May 29, 2018, 01:32 PM
• Last activity: Jan 26, 2025, 09:30 PM
1
votes
1
answers
496
views
Unable to mount/unlock encrypted APFS volume
I have an external disk that's APFS-encrypted which suddenly won't mount/unlock: $ diskutil apfs unlockVolume /dev/disk7s1 -nomount Passphrase: Unlocking any cryptographic user on APFS Volume disk7s1 Passphrase incorrect or user does not exist I also can't modify the APFS container from Disk Utility...
I have an external disk that's APFS-encrypted which suddenly won't mount/unlock:
$ diskutil apfs unlockVolume /dev/disk7s1 -nomount
Passphrase:
Unlocking any cryptographic user on APFS Volume disk7s1
Passphrase incorrect or user does not exist
I also can't modify the APFS container from Disk Utility to add any new volumes.
I thought maybe corruption had led to my password no longer unlocking the files, but I downloaded DiskDrill, supplied it with my password and let it scan for files and it actually found them!
I'm wondering if that means the partition table is messed up or something, because obviously the passphrase is still decrypting the files. I don't have enough disk space on hand to recover these files and re-create the APFS volume right now - any help would be appreciated. I've tried to interpret these hex dumps using GPT header and table lookup information but I'm not making much progress.
Edit 1: I've added fsck_apfs output, and I think the issue is the space manager data in the container, not the volume itself. I would be happy to roll this container back to a different, healthier checkpoint but I'm not sure how.
**Diskutil**
$ diskutil list
[...]
/dev/disk6 (internal, physical):
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *1.0 TB disk6
1: EFI EFI 209.7 MB disk6s1
2: Apple_APFS Container disk7 1.0 TB disk6s2
/dev/disk7 (synthesized):
#: TYPE NAME SIZE IDENTIFIER
0: APFS Container Scheme - +1.0 TB disk7
Physical Store disk6s2
1: APFS Volume Storage 419.8 GB disk7s1
**GPT**
$ sudo gpt -r show disk7
start size index contents
0 1 PMBR
1 1 Pri GPT header
2 32 Pri GPT table
34 6
40 409600 1 GPT part - C12A7328-F81F-11D2-BA4B-00A0C93EC93B
409640 1954135984 2 GPT part - 7C3457EF-0000-11AA-AA11-00306543ECAC
1954545624 7
1954545631 32 Sec GPT table
1954545663 1 Sec GPT header
**GPT Header**
$ sudo dd if=/dev/disk6 bs=512 count=1 skip=1 | hexdump -Cv
00000000 45 46 49 20 50 41 52 54 00 00 01 00 5c 00 00 00 |EFI PART....\...|
00000010 05 ac dd 9f 00 00 00 00 01 00 00 00 00 00 00 00 |................|
00000020 ff ff 7f 74 00 00 00 00 22 00 00 00 00 00 00 00 |...t....".......|
00000030 de ff 7f 74 00 00 00 00 86 e8 09 f7 47 a3 31 48 |...t........G.1H|
00000040 ab b1 17 2f 5e b4 24 6e 02 00 00 00 00 00 00 00 |.../^.$n........|
00000050 80 00 00 00 80 00 00 00 2b 1a b5 ae 00 00 00 00 |........+.......|
00000060 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000070 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000080 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000090 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000100 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000120 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000200
**GPT Table**
$ sudo dd if=/dev/disk6 bs=512 count=1 skip=2 | hexdump -Cv
00000000 28 73 2a c1 1f f8 d2 11 ba 4b 00 a0 c9 3e c9 3b |(s*......K...>.;|
00000010 27 f8 f8 1b af 49 81 44 99 e7 32 45 65 64 2b ee |'....I.D..2Eed+.|
00000020 28 00 00 00 00 00 00 00 27 40 06 00 00 00 00 00 |(.......'@......|
00000030 00 00 00 00 00 00 00 00 45 00 46 00 49 00 20 00 |........E.F.I. .|
00000040 53 00 79 00 73 00 74 00 65 00 6d 00 20 00 50 00 |S.y.s.t.e.m. .P.|
00000050 61 00 72 00 74 00 69 00 74 00 69 00 6f 00 6e 00 |a.r.t.i.t.i.o.n.|
00000060 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000070 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000080 ef 57 34 7c 00 00 aa 11 aa 11 00 30 65 43 ec ac |.W4|.......0eC..|
00000090 c1 c6 8d 57 81 82 e9 4c a3 7d fa d0 2f b7 bd 74 |...W...L.}../..t|
000000a0 28 40 06 00 00 00 00 00 d7 ff 7f 74 00 00 00 00 |(@.........t....|
000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000100 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000120 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000200
**GPT Partition 1**
$ sudo dd if=/dev/disk6 bs=512 count=1 skip=40 | hexdump -Cv
00000000 eb 58 90 42 53 44 20 20 34 2e 34 00 02 01 20 00 |.X.BSD 4.4... .|
00000010 02 00 00 00 00 f0 00 00 20 00 10 00 00 00 00 00 |........ .......|
00000020 00 40 06 00 4f 0c 00 00 00 00 00 00 02 00 00 00 |.@..O...........|
00000030 01 00 06 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000040 00 00 29 ed 17 e3 67 45 46 49 20 20 20 20 20 20 |..)...gEFI |
00000050 20 20 46 41 54 33 32 20 20 20 fa 31 c0 8e d0 bc | FAT32 .1....|
00000060 00 7c fb 8e d8 e8 00 00 5e 83 c6 19 bb 07 00 fc |.|......^.......|
00000070 ac 84 c0 74 06 b4 0e cd 10 eb f5 30 e4 cd 16 cd |...t.......0....|
00000080 19 0d 0a 4e 6f 6e 2d 73 79 73 74 65 6d 20 64 69 |...Non-system di|
00000090 73 6b 0d 0a 50 72 65 73 73 20 61 6e 79 20 6b 65 |sk..Press any ke|
000000a0 79 20 74 6f 20 72 65 62 6f 6f 74 0d 0a 00 00 00 |y to reboot.....|
000000b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000100 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000120 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 aa |..............U.|
00000200
**GPT Partition 2**
$ sudo dd if=/dev/disk6 bs=512 count=1 skip=409640 | hexdump -Cv
00000000 65 f1 69 6d 45 1d 32 73 01 00 00 00 00 00 00 00 |e.imE.2s........|
00000010 a8 94 00 00 00 00 00 00 01 00 00 80 00 00 00 00 |................|
00000020 4e 58 53 42 00 10 00 00 f6 37 8f 0e 00 00 00 00 |NXSB.....7......|
00000030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000040 02 00 00 00 00 00 00 00 a6 87 6e b0 9d 7a 46 9f |..........n..zF.|
00000050 9f da 0f e9 af ae 73 d2 76 de 00 00 00 00 00 00 |......s.v.......|
00000060 a9 94 00 00 00 00 00 00 18 01 00 00 5c 6c 00 00 |............\l..|
00000070 01 00 00 00 00 00 00 00 19 01 00 00 00 00 00 00 |................|
00000080 0d 01 00 00 85 16 00 00 0b 01 00 00 02 00 00 00 |................|
00000090 79 16 00 00 0c 00 00 00 00 04 00 00 00 00 00 00 |y...............|
000000a0 f7 a5 11 00 00 00 00 00 01 04 00 00 00 00 00 00 |................|
000000b0 00 00 00 00 64 00 00 00 02 04 00 00 00 00 00 00 |....d...........|
000000c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000000f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000100 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000120 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001c0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000001f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000200
**fsck_apfs output**
$ sudo fsck_apfs -F -n /dev/disk6s2
** Checking the container superblock.
Checking the checkpoint with transaction ID 38056.
** Checking the space manager.
warning: spaceman chunk 50 free count 1048041 > block count 32768
warning: spaceman chunk 76 free count 1047379 > block count 32768
warning: spaceman chunk 77 free count 1045263 > block count 32768
warning: spaceman chunk 81 free count 1047089 > block count 32768
warning: spaceman chunk 88 free count 1046859 > block count 32768
warning: spaceman chunk 95 free count 1048285 > block count 32768
warning: spaceman chunk 96 free count 1045846 > block count 32768
warning: spaceman chunk 106 free count 1038642 > block count 32768
warning: spaceman chunk 107 free count 1047917 > block count 32768
warning: spaceman chunk 108 free count 1048545 > block count 32768
warning: spaceman chunk 118 free count 1042009 > block count 32768
warning: spaceman chunk 120 free count 1047762 > block count 32768
warning: spaceman chunk 121 free count 1044764 > block count 32768
warning: spaceman chunk 159 free count 1043537 > block count 32768
warning: spaceman chunk 192 free count 1048119 > block count 32768
warning: spaceman chunk 197 free count 1047955 > block count 32768
warning: spaceman chunk 198 free count 1031491 > block count 32768
warning: spaceman chunk 214 free count 1020054 > block count 32768
warning: spaceman chunk 220 free count 1045881 > block count 32768
warning: spaceman chunk 234 free count 1046468 > block count 32768
warning: spaceman chunk 257 free count 1048280 > block count 32768
warning: spaceman chunk 270 free count 1045917 > block count 32768
warning: spaceman chunk 280 free count 1048521 > block count 32768
warning: spaceman chunk 288 free count 1047651 > block count 32768
warning: spaceman chunk 289 free count 1044620 > block count 32768
warning: spaceman chunk 294 free count 1046582 > block count 32768
warning: spaceman chunk 304 free count 1037560 > block count 32768
warning: spaceman chunk 305 free count 1047826 > block count 32768
warning: spaceman chunk 328 free count 1048515 > block count 32768
warning: spaceman chunk 330 free count 1045119 > block count 32768
warning: spaceman chunk 333 free count 1046817 > block count 32768
warning: spaceman chunk 334 free count 1047085 > block count 32768
warning: spaceman chunk 335 free count 1047577 > block count 32768
warning: spaceman chunk 336 free count 1037524 > block count 32768
warning: spaceman chunk 338 free count 1047719 > block count 32768
warning: spaceman chunk 342 free count 1047582 > block count 32768
warning: spaceman chunk 345 free count 1048065 > block count 32768
warning: spaceman chunk 348 free count 1046590 > block count 32768
warning: spaceman chunk 351 free count 1048000 > block count 32768
warning: spaceman chunk 354 free count 1048325 > block count 32768
warning: spaceman chunk 359 free count 1047571 > block count 32768
warning: spaceman chunk 360 free count 1048574 > block count 32768
warning: spaceman chunk 362 free count 1045869 > block count 32768
warning: spaceman chunk 364 free count 1023077 > block count 32768
warning: spaceman chunk 366 free count 1047638 > block count 32768
warning: spaceman chunk 368 free count 1047692 > block count 32768
warning: spaceman chunk 370 free count 1047439 > block count 32768
warning: spaceman chunk 373 free count 1048521 > block count 32768
warning: spaceman chunk 376 free count 1044611 > block count 32768
warning: spaceman chunk 379 free count 1039521 > block count 32768
Too many warnings of this type generated; suppressing subsequent ones.
warning: (oid 0x6f84) cib: invalid o_cksum (0xffffffffffffffff)
error: failed to read spaceman cib 27 at address 0x6f84
Space manager is invalid.
** The container /dev/disk6s2 could not be verified completely.
Harv
(5800 rep)
Sep 2, 2024, 09:46 PM
• Last activity: Jan 14, 2025, 03:53 AM
1
votes
1
answers
203
views
Correct password not accepted for first login after reboot - filevault off
Edit for conciseness: Macbook Pro Intel T2 from 2018, latest available MacOs 14. 2 Accounts existing, both admin. My primary account has recently been changed from restricted to admin. This is not confirmed temporally related to the problem. After reboot one of the accounts can't be logged in. Only...
Edit for conciseness:
Macbook Pro Intel T2 from 2018, latest available MacOs 14.
2 Accounts existing, both admin.
My primary account has recently been changed from restricted to admin.
This is not confirmed temporally related to the problem.
After reboot one of the accounts can't be logged in. Only after another user was logged in first, I can use the password to login the primary account.
I thought it was related to Filevault.
But even with Filevault off, it behaves the same.
Machine has never seen any MDM or special fiddling with user properties. No Icloud connected.
Changing the users password does not have any effect in this.
Newly created accounts do not have this issue. Only this one account.
Testing this is time consuming because of the imo very aggressive ratelimiter.
Occasionally even on a reboot after a logged in session of the primary user, will that user be locked from anything from 15min to over an hour. Without even inputting a wrong password once.
What could be wrong with the account? How could I fix this without migrating to a new account.
Edit:
Will copying the directories to a new user with same uid and name port everything?
What about keyring, wifi credentials, vpn, dev certificates?
Yet another edit:
A Yubikey was paired with the account. After unpairing it, reboot and the whole yadda. I had yet again got a 15 min wait until I could try entering the password. And then it actually worked.
Then I turned Filevault back on. And it does not work anymore.
Frustration 100
Old:
*My Macbook suddenly stopped accepting my account password to first unlock the machine from filevault.
Another account still works to unlock filevault.
After unlocking filevault I can login to that user with the correct password.
After login I tried changing the password. The correct password was accepted as correct password.
It still won't unlock on fresh boot with the correct password.
Now I had a ratelimit of half a day.
It seems the filevault ratelimiter never got reset. Even tho I logged in using another account.
So after FV unlock, pw works. Before FV unlock, pw does not work.
Turning Filevault off and on again to rebuild the key wrangling machines' derivation data from the password again did not work.
Changing the password because maybe just on/off doesn't rebuild the key derivation data did not work. I have got another account lock for quite a time again.
Even with Filevault disabled, first login after reboot does not work with the weird user.
I also never did any MDM like stuff nor manully screwed around with policy settings.
The only thing special about the account is, that it was once restricted user and was upgraded to admin recently.
I can't tell if the problem happened at the exact time of changing that.
After last login with FV off after logging in to the working user, even tho not once failing input during that boot, the weird account still had a 15 min block on it before I could try. Even tho I rebooted from a logged in session of that account.
What do?*
Unbuu
(11 rep)
Dec 15, 2024, 03:37 AM
• Last activity: Dec 16, 2024, 06:05 AM
1
votes
0
answers
197
views
Why does updating macOS keep changing my FileVault recovery key?
I have an M1 Mac Mini running macOS 14 Sonoma. Every time I've done a minor system update on it, like from 14.0 to 14.1, or 14.6 to 14.7, and so on, it tells me that there's a new FileVault recovery key. It's happened every single time. This is not only annoying, but it makes it a lot more likely I'...
I have an M1 Mac Mini running macOS 14 Sonoma. Every time I've done a minor system update on it, like from 14.0 to 14.1, or 14.6 to 14.7, and so on, it tells me that there's a new FileVault recovery key. It's happened every single time.
This is not only annoying, but it makes it a lot more likely I'll lose access to this system should I need to use the recovery key, because if I have to keep writing down a new one, it makes it that much more likely I'll accidentally copy it down wrong (because of course you can't copy the key to the clipboard) or lose it somehow.
I'm sure this is not intended behavior. The recovery key is supposed to remain consistent. How can I fix this?
Bri Bri
(2930 rep)
Oct 30, 2024, 06:01 PM
4
votes
2
answers
5677
views
FileVault2: how do I use the recovery key when asked for a "Disk Password"?
I've got a MacBook Pro protected with FileVault 2 (10.9), and can't remember the password to unlock the disk. When I boot, it asks for the "Disk Password". What I have is the recovery key that I printed on paper when I activated FileVault. How do I use it ? Entering a wrong password multiple times d...
I've got a MacBook Pro protected with FileVault 2 (10.9), and can't remember the password to unlock the disk.
When I boot, it asks for the "Disk Password".
What I have is the recovery key that I printed on paper when I activated FileVault.
How do I use it ?
Entering a wrong password multiple times doesn't prompt for the recovery key, and sometimes a '?' appears but it doesn't do anything.
(I've read http://support.apple.com/kb/ht4790 , but it doesn't explain how to use the recovery key.)
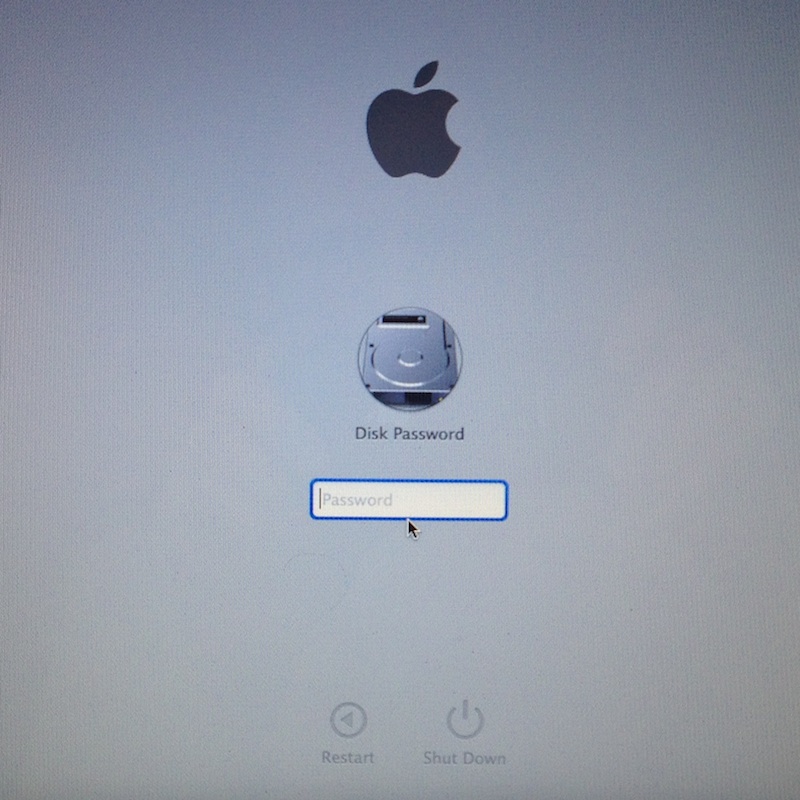
Charles François Rey
(41 rep)
Apr 19, 2014, 07:55 AM
• Last activity: Oct 23, 2024, 11:21 AM
0
votes
1
answers
41
views
Access log for encrypted thumb drive
I have a USB thumb drive that’s encrypted using Disk Utility standard encryption, so the drive requires a password to access the data/files. My question is, is there a log of each time the USB drive is accessed, mounted to a computer, or opened? If I plug it in, type in the password, and access the...
I have a USB thumb drive that’s encrypted using Disk Utility standard encryption, so the drive requires a password to access the data/files.
My question is, is there a log of each time the USB drive is accessed, mounted to a computer, or opened?
If I plug it in, type in the password, and access the files, will I be able to see the last time the drive was accessed? (Logged into).
Is the history log only available if the thumb drive is plugged into the same computer or is the history there for anyone with the password?
BW801
(1 rep)
Oct 6, 2024, 07:52 PM
• Last activity: Oct 7, 2024, 12:00 AM
Showing page 1 of 20 total questions